Researchers have uncovered a massive campaign that delivered proxy server apps to at least 400,000 Windows systems. The devices act as residential exit nodes without users’ consent and a company is charging for the proxy traffic running through the machines..
Residential proxies are valuable to cybercriminals because they can help with deploying large-scale credential stuffing attacks from fresh IP addresses. They also have legitimate purposes like ad verification, data scraping, website testing, or privacy-enhancing rerouting.
The proxy client establishes persistence on the infected system by creating a registry key to activate it when the system boots and a by adding a scheduled task that to check for new client updates.
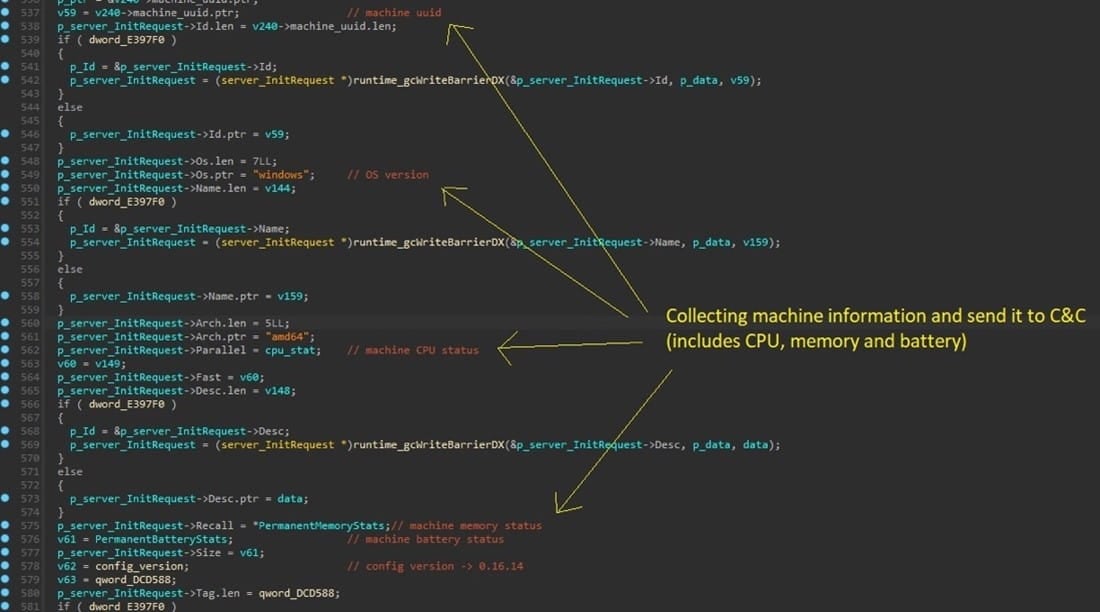
“The proxy then continuously gathers vital information from the machine to ensure optimal performance and responsiveness,” explains the AT&T report.
“This includes everything from the process list and monitoring CPU to memory utilization and even tracking battery status.”
How to protect
AT&T recommends looking for a “Digital Pulse” executable at “%AppData%\” or a similarly named Registry key on “HKCU\Software\Microsoft\Windows\CurrentVersion\Run\.” If any are present, the researchers recommend removing them.
The name of the scheduled task is “DigitalPulseUpdateTask” and should also be deleted to eliminate the chance of the client update mechanism re-introducing the infection.
Finally, avoid downloading pirated software and running executables sourced from dubious locations like peer-to-peer networks or site offering premium software free of charge.
Signs of proxyware infection include performance and internet speed degradation, unexpected network traffic patterns, frequent communication with unknown IPs or domains, and system alerts.
Reference: https://www.bleepingcomputer.com/news/security/massive-400-000-proxy-botnet-built-with-stealthy-malware-infections/
AH




