New research conducted by cybersecurity firm, Armis, has found that UK organisations are currently facing a heightened cybersecurity risk due to several key factors. These include the complexities brought on by a heightened regulatory environment, recruitment and staffing difficulties, an ever-increasing attack surface as well as a lack of updated inventory information. The research reveals that while prioritization of threat intelligence has become important, infrequent updates of inventory information and a skewed view of what is connected to the network made worse by the increasing number of attacks means that security breaches are becoming more common and there is a growing sense of urgency to address this.
Curtis Simpson, Chief Information Security Officer at Armis, notes that given the complexity and evolving nature of technology environments, “security programs cannot run on intuition” and businesses require continuous visibility and intelligence, particularly where technical assets powering the business are concerned, to understand how the corresponding attack surface can or is being exploited.
Amris’ research on the current cybersecurity landscape in the UK found that top priorities for professionals in the past six months involved keeping up with threat intelligence, ensuring compliance with cybersecurity regulations and frameworks, staffing and recruitment, and managing the ever expanding attack surface. Other key concerns included visibility into all assets connected to the network as well as securing the supply chain and the convergence between IT and OT. Respondents revealed various strategies including verifying access control and reviewing employee passwords, high severity alerts, and creating or updating the company incident response plan to tackle the extensive risks.
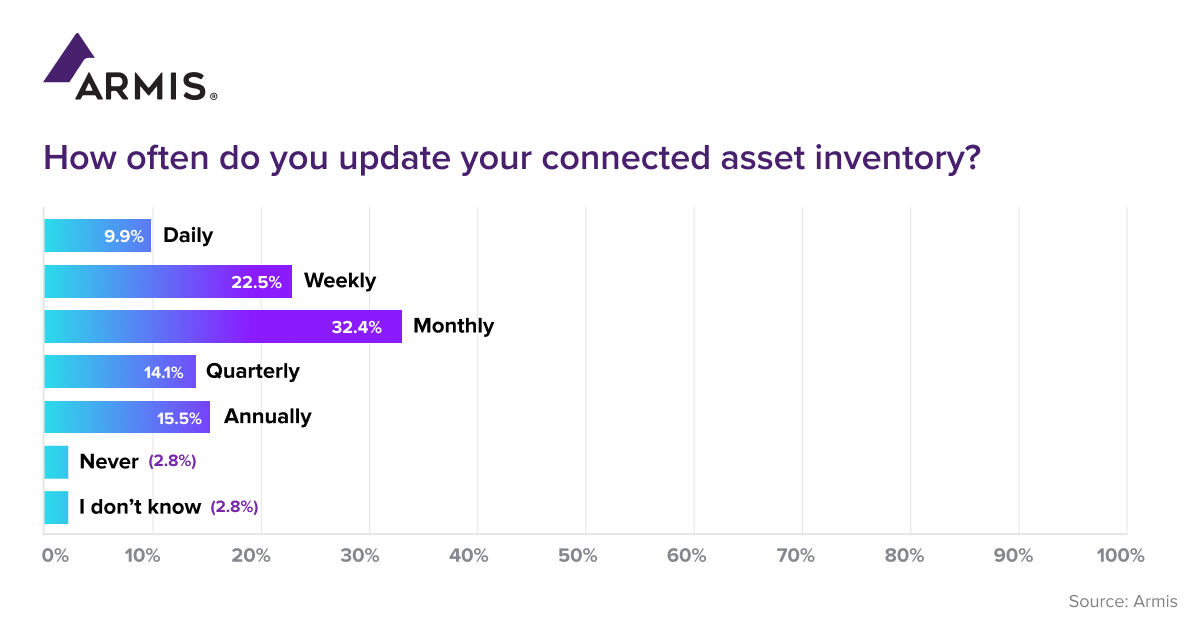
Despite the numerous complexities, the research indicated that over 60% of organisations use more than five tools, in some cases as many as fifty, to monitor their connected assets whilst nearly 30% of respondents use Configuration Management Database (CMDB) solutions. Disturbingly, however, when asked how often they updated the inventory of assets connected to their network, over 15% of respondents said annually, whilst over 30% said monthly, and over 20% said weekly. Only 10% of respondents said they updated their inventory on a daily basis, while nearly 3% answered never.
Data collected between January and April 2023 on the proprietary Armis Asset Intelligence and Security Platform showed that 53% of Armis’ customer base had more than 35,000 devices on their network, while 35% had more than 100,000 network devices. In contrast, 96% of respondents believed they had 35,000 or less devices on their network, revealing that several organisations could be unaware of their actual inventory due to the limitations and infrequency of information updates available.
Further findings highlighted that over half of the respondents reported suffering breaches or ransomware attacks in the past five years, with employee phishing being the primary cause of the breach in over 43% of cases and IoT device hacks contributing to around 23% of incidents. Unsurprisingly, known vulnerabilities that had not been patched, as well as unpatched devices, were also revealed as significant attack vectors.
Armis notes that the data reinforces that organisations are currently struggling to monitor all devices in their operational environment, which has made prioritisation a challenge. Thus, there is a need to have a comprehensive view of all the assets in the user’s environment, as well as an understanding of asset behaviour, which ensures quick identification of risks and effective prioritisation of remediation efforts.
This report provides a timely reminder to organisations in the UK to ensure they have up-to-date inventory information with comprehensive visibility and retention of behaviour-based asset insights. They are also encouraged to adopt security intelligence solutions with real-time monitoring abilities that will detect suspicious activities and identify potentially vulnerable endpoints. Such measures will help organisations significantly reduce their cybersecurity risk, guard against attacks, securely manage inventory, and boost security posture overall.