A critical remote code execution (RCE) vulnerability in Zimbra email servers has been exploited and users are advised to take immediate action. Zimbra, a widely targeted platform for hackers, has seen numerous vulnerabilities listed by CISA in their Known Exploited Vulnerabilities catalog. The latest vulnerability (CVE-2024-45519) has already been exploited by attackers, with over 90,000 web-exposed Zimbra servers at risk.
Researchers have identified the vulnerability in Zimbra’s postjournal SMTP parsing service as critical, even before official ratings were assigned. A Proof of Concept (PoC) shared by ProjectDiscovery researchers demonstrated how the vulnerability could be abused through specially crafted emails, leading to immediate exploitation.
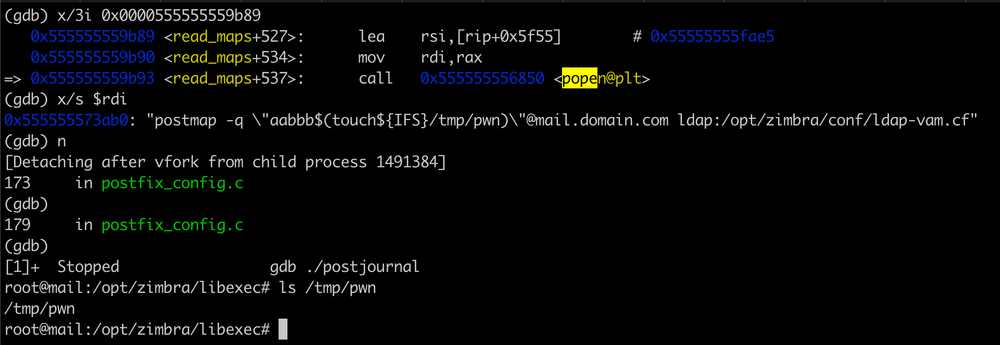
Security expert Will Dormann described the Zimbra flaw as an “embarrassingly bad vulnerability” due to the way it handles email addresses and runs commands using shell escape characters. The vulnerability allows unsanitized user input to be passed to popen, enabling attackers to inject arbitrary commands. The exploit was found to be quite simple, as the vulnerable code executes any commands specified in the email address.
Malicious emails exploiting the vulnerability have been traced back to specific IP addresses, with attackers leveraging the Zimbra postjournal service to inject commands. Researchers found that the postjournal binary lacked crucial security measures like execvp or run_command functions, leaving it vulnerable to direct command injections.
Soon after the PoC was made public, Proofpoint researchers observed the vulnerability being actively exploited, with attackers sending spoofed emails to trigger command execution on vulnerable Zimbra servers. Some of these emails were used to create webshells on compromised servers, enabling further malicious activities.
To mitigate the risk posed by this vulnerability, Zimbra administrators are advised to disable the postjournal service if not required, configure mynetworks settings to prevent unauthorized access, and apply the latest security updates provided by Zimbra. The severity of the vulnerability, rated a perfect 10.0 by MITRE, underscores the importance of immediate patching to prevent further attacks.
In conclusion, the active exploitation of the Zimbra vulnerability highlights the ongoing threat posed by RCE vulnerabilities in email servers. With attackers targeting vulnerable systems at an alarming rate, users and administrators must stay vigilant and prioritize security measures to safeguard their systems and sensitive data.