A new malware campaign named OBSCURE#BAT has emerged, exploiting social engineering tactics and fake software downloads to deceive users, steal data, and remain undetected on systems. Cybersecurity researchers at Securonix Threat Labs have identified this threat and warned users about the dangers posed by this malicious campaign.
The attack begins when a user unwittingly executes a malicious batch file, which is often disguised as legitimate security features or software downloads. Once the malware is executed, it establishes itself by creating scheduled tasks and manipulating the Windows Registry to ensure persistence even after system reboots.
To avoid detection, the malware utilizes a user-mode rootkit to conceal its presence on the system. This rootkit is capable of hiding files, registry entries, and running processes, making it challenging for users and security tools to detect the malicious activity. By embedding itself into legitimate system processes and services, the malware can evade detection and continue its nefarious operations.
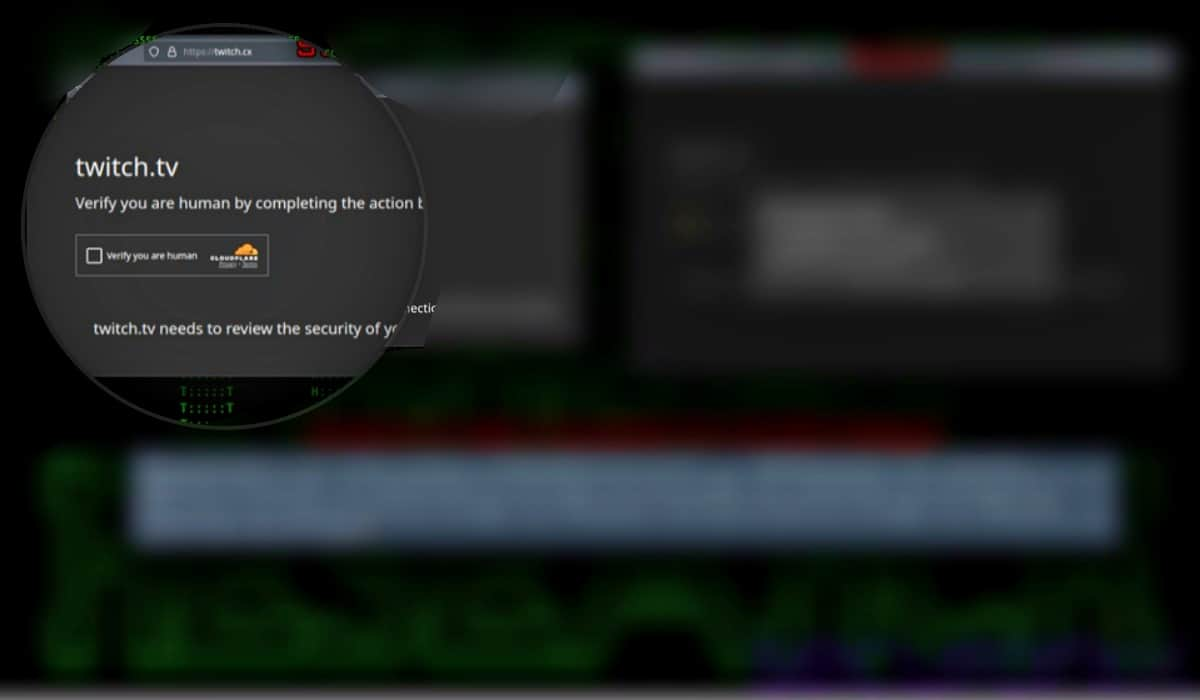
Similar to recent campaigns, the OBSCURE#BAT malware campaign leverages fake captchas and malicious software downloads to lure users into executing the malicious code. Attackers disguise their files as legitimate applications, such as Tor Browser or Adobe products, increasing the likelihood of users falling victim to the scam. Fake captchas, especially those imitating Cloudflare’s captcha feature, trick users into executing the malicious code, leading to further exploitation of their systems.
The evasion techniques employed by the OBSCURE#BAT malware campaign pose a significant threat to both individuals and organizations. By using API hooking, the malware hides its files, registry entries, and running processes from common tools like Windows Task Manager, making detection more difficult. Additionally, the malware manipulates the registry by registering a fake driver to ensure persistence and implements stealthy logging to monitor user interactions, further complicating detection and analysis.
Securonix’s detailed technical report reveals that the OBSCURE#BAT malware campaign primarily targets users in countries like Canada, Germany, the United States, and the United Kingdom. The motives behind the attack seem to be financially motivated or espionage-related, underscoring the severity of the threat posed by this malware campaign.
To protect themselves from the OBSCURE#BAT attack and similar threats, users and organizations are advised to follow key security measures. These include downloading software only from legitimate sources, deploying endpoint logging tools for enhanced detection capabilities, monitoring systems for suspicious activity, and utilizing threat detection tools such as behavioral analysis and machine learning-based systems.
By staying vigilant and implementing cybersecurity best practices, users can safeguard themselves against the dangers posed by the OBSCURE#BAT malware campaign and protect their systems from potential compromise.