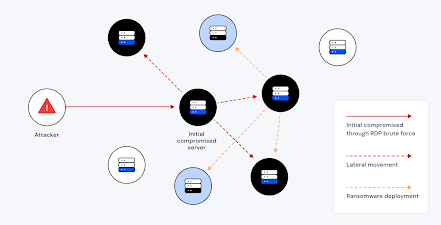
Most businesses treat breaches as perimeter problems — patch the firewall, update the antivirus, sleep better at night. But the real threat isn’t how attackers get in — it’s what they do after they’re already inside. That’s the brutal reality of lateral movement, and a recent Global Cloud Detection and Response Report confirms it remains the toughest threat for security teams to spot and stop.
Lateral movement isn’t just a fancy buzzword — it’s the phase of a cyberattack where an intruder navigates sideways across systems after gaining initial access. Instead of blasting past perimeter defenses, they quietly escalate privileges, harvest credentials, and hop from one asset to the next. Attackers use legitimate credentials and built-in tools like PowerShell, RDP or SMB to mask their activity, making them extremely difficult to detect.
Why does this matter? Because once attackers move laterally:
-
They can reach your crown jewels — databases, domain controllers, backups. Huntress
-
They stay hidden for longer, dramatically increasing the damage they can do. Illumio
-
They dramatically increase the cost and time to respond. Fidelis Security
What This Means for Your Security Strategy
If your cyber defenses are built around perimeter security, you’re already behind. What matters now is visibility, context, and speed:
-
Visibility across hybrid environments: attackers don’t care if parts of your network are on-premises or in the cloud — you need eyes everywhere. B2B Cyber Security
-
Context-rich alerts: not just alarms, but meaning — so your team can act instead of triage. B2B Cyber Security
-
Zero trust and micro-segmentation: assume nothing inside the network is safe until proven otherwise. Netwrix
https://b2b-cyber-security.de/en/Lateral-movement-remains-the-greatest-cyber-risk/