A recent discovery regarding a vulnerability in Kia cars has shed light on the potential risks associated with the increasing connectivity of everyday devices to the internet. This particular vulnerability, which has already been addressed by Kia through a patch, allowed attackers to easily obtain the vehicle identification number (VIN) from the license plate and subsequently register themselves as the car’s owner on Kia’s network. The details of this hack and the timeline of its discovery can be found on Sam Curry’s website.
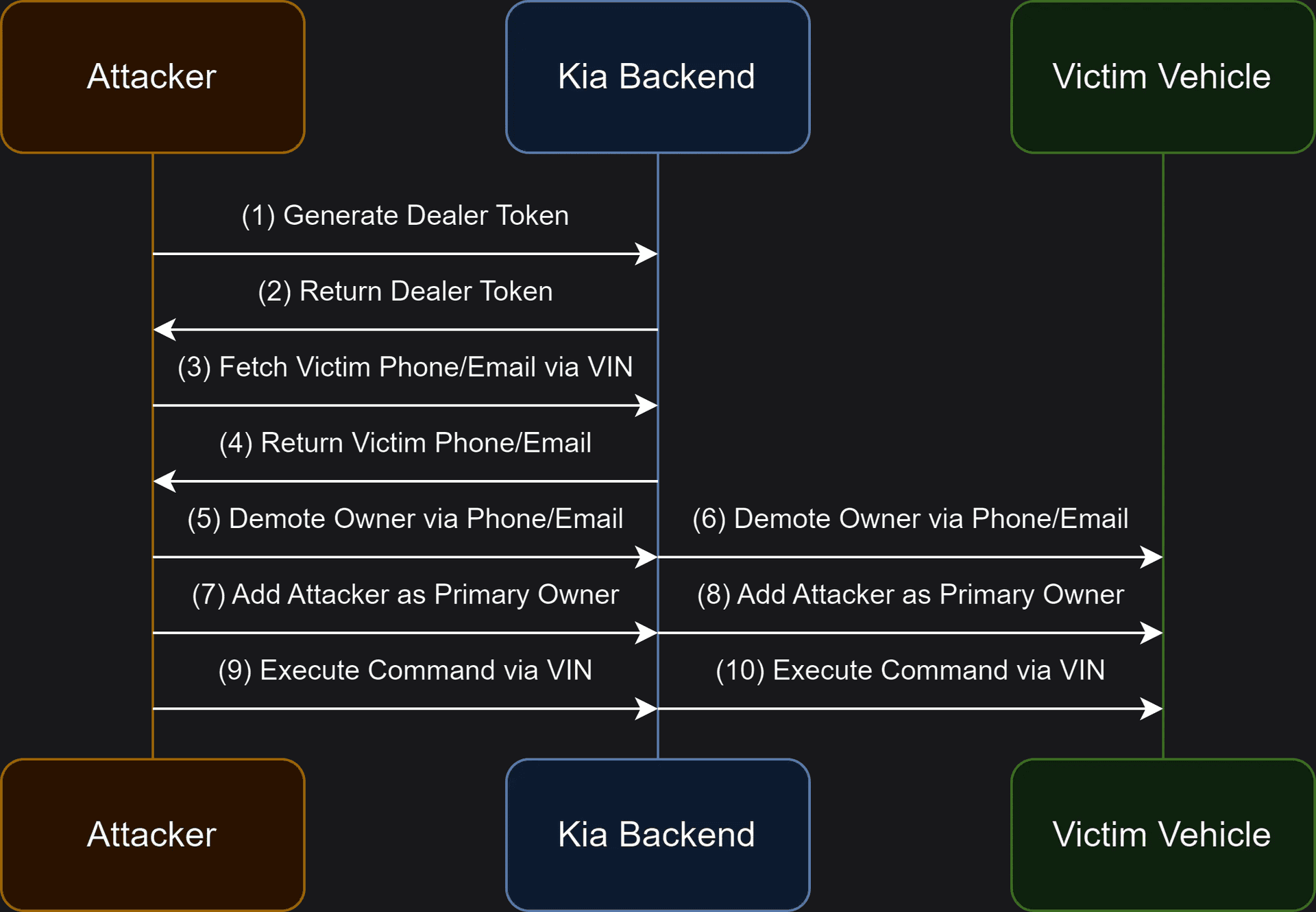
This incident is not the first time vulnerabilities have been found in Kia’s HTTP-based APIs. This time, the attack targeted dealer endpoints, enabling the attacker to register as a dealer and acquire a valid session ID to access user information such as email addresses and phone numbers from Kia’s systems. By using a specially crafted tool to automate the process, the attacker could then take over as the primary owner of the car, granting them control over functions like locking/unlocking doors, honking the horn, locating the vehicle, and starting/stopping the engine. The vulnerability affected all Kia cars produced after 2013, with victims often unaware that their vehicles had been compromised.
One of the most alarming aspects of this vulnerability is the potential for a thief to identify a vulnerable parked car, gain access, start the engine, and drive away without the owner’s knowledge. As long as remote APIs continue to offer such levels of control, there is a pressing need for car manufacturers to prioritize security measures. This case is just one example in a long line of security vulnerabilities that can be exploited by hackers equipped with simple HTTP query tools.
It is imperative that companies take proactive measures to secure their products and services, especially as the IoT (Internet of Things) landscape continues to expand. Consumers rely on the convenience and efficiency of connected devices, but these benefits come with inherent risks if proper security protocols are not in place. As technology evolves, so too should our approaches to safeguarding against cyber threats. The Kia vulnerability serves as a reminder of the importance of robust cybersecurity measures in an increasingly interconnected world.
In conclusion, the incident with Kia cars highlights the need for heightened vigilance and proactive security measures in the face of evolving cyber threats. While the vulnerability has been addressed, it underscores the vulnerabilities that can arise with internet-connected devices and the importance of safeguarding against potential exploits. As technology advances, so must our defenses against malicious actors seeking to exploit vulnerabilities for their own gain. It is crucial for companies and consumers alike to prioritize cybersecurity in an age where connectivity is the norm.