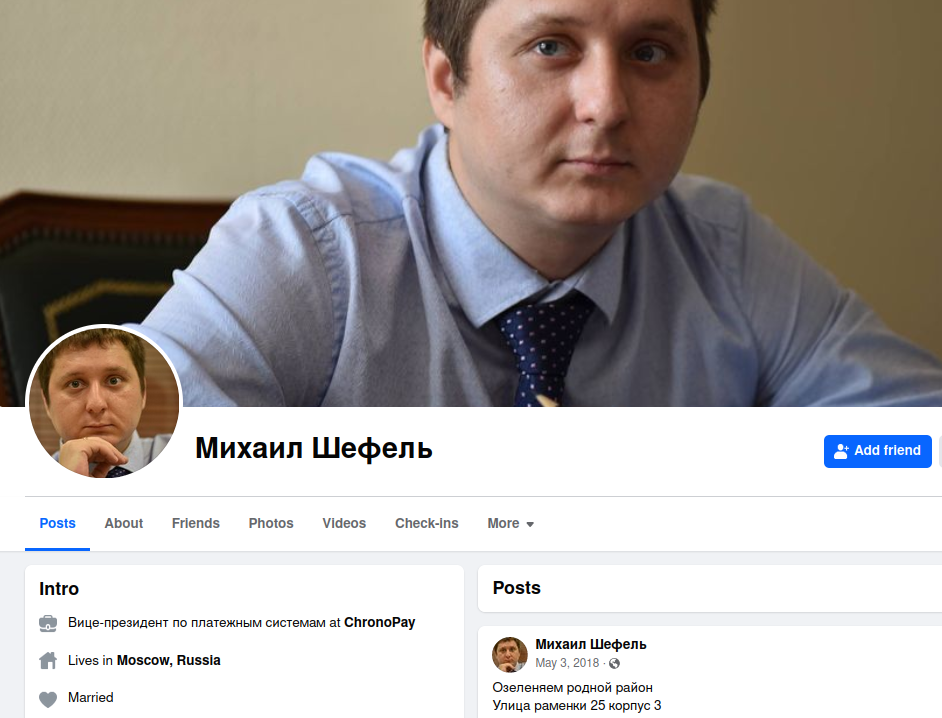
In December 2023, the true identity of Rescator, a Russian cybercriminal responsible for selling more than 100 million payment cards stolen from Target and Home Depot between 2013 and 2014, was revealed by KrebsOnSecurity. The man behind the Rescator nickname was identified as Moscow resident Mikhail Shefel, who had recently changed his legal surname to Lenin. Shefel, in a recent interview, confessed to using the Rescator moniker and admitted that he had reached out for publicity due to financial struggles and the desire to promote several new money-making ventures.
The 38-year-old Shefel was previously featured in a 2023 news story about the Target breach investigation, detailing his past involvement as the vice president of payments at ChronoPay, a Russian financial company known for supporting fraudulent activities such as fake antivirus scams and knockoff pharmaceuticals. Shefel’s connection to the Rescator identity and his collaboration with a sanctioned Russian individual named Aleksandr Ermakov, who was involved in a data breach at Medibank, raised questions about his involvement in cybercrime.
Despite previous attempts to contact Shefel for comment, he remained silent until KrebsOnSecurity reported on his connection to the theft of Social Security and tax information from South Carolina residents in 2012. Following this report, Shefel initiated communication with the author to clarify his alleged criminal activities in the hacking world. In a series of video chats and messages, Shefel confirmed his ties to the Rescator identity and his involvement in operating websites that sold stolen payment card data from various retail chains.
Shefel claimed that the actual mastermind behind the Target and Home Depot breaches was a Ukrainian hacker named Dmitri Golubov, who he alleged was responsible for the card-stealing malware used in the attacks. Shefel, who formerly worked as the technical director of a Russian cybercrime community called Lampeduza, also mentioned his collaboration with Golubov in developing the malicious software that targeted payment terminals.
As Shefel shared insights into his hacking career and collaborations with other cybercriminals, including the introduction of Rescator to another hacker named Helkern, he also disclosed his financial struggles and past business ventures. From selling stolen payment cards to investing in a now-defunct search engine and running a click-advertising business, Shefel highlighted his changing fortunes in the cyber underworld.
The revelation of Shefel’s involvement in a ransomware affiliate program called Sugar, which led to his arrest alongside Ermakov, added a new layer of complexity to his story. Shefel’s claims of being set up by Peter Vrublevsky, the son of his former boss at ChronoPay, and facing prosecution in Moscow for the ransomware operation shed light on the interconnected web of cybercrime in Russia.
Furthermore, Shefel’s insights into the criminal activities of Vrublevsky and his alleged involvement in illicit markets such as Sprut, a successor to the Hydra darknet marketplace, highlighted the broader implications of cybercrime in Russia. Shefel’s portrayal of himself as a struggling coder looking for new business opportunities underscored the challenges faced by individuals in the cybercriminal ecosystem.
Overall, Shefel’s story sheds light on the complex world of cybercrime, the blurred lines between legitimate and illicit businesses, and the personal struggles of individuals caught in the web of digital deception. His journey from a prominent cybercriminal to a financially strained coder seeking redemption and stability reflects the ever-evolving landscape of cyber threats and the individuals behind them.