The UAC-0057 hacking collective, also known as GhostWriter, has resurfaced in the cyber threat landscape. They have been taking advantage of a zero-day vulnerability in WinRAR, identified as CVE-2023-38831, which has been actively exploited between April and August 2023. By exploiting this vulnerability, the hackers are able to infect targeted systems with the PicassoLoader variant and Cobalt Strike Beacon malware. It’s worth noting that UAC-0057 previously used these malicious strains in attacks during the summer of 2023, specifically targeting the Ukrainian government and educational sector.
Recently, the CERT-UA team issued a warning about an ongoing attack on Ukraine carried out by UAC-0057, also known as GhostWriter. This malicious campaign involves the abuse of CVE-2023-38831, a zero-day vulnerability that affects earlier versions of the WinRAR software. This vulnerability allows threat actors to execute arbitrary code when a user attempts to view a file from a corresponding ZIP archive. The PoC (Proof of Concept) exploit for CVE-2023-38831 has been made publicly available on GitHub, and there has been a notable increase in exploitation attempts since August 2023, posing risks to stock brokers and traders globally.
In this latest campaign targeting Ukraine, the hackers exploit the WinRAR security vulnerability by using an archive file containing the CVE-2023-38831 exploit. Once successfully exploited, the attackers execute a CMD file, which then launches an LNK file. This LNK file runs an HTA file through the mshta.exe utility. This leads to the creation of a PDF lure with a filename related to the Russia-Ukraine war, and then malicious JavaScript code is executed on the compromised systems. The JavaScript code is another variant of PicassoLoader, previously used by UAC-0057 in their offensive campaigns against Ukraine. It is designed to download an SVG lure image and decrypt a malicious .NET file that utilizes the Rabbit encryption algorithm. The .NET file ultimately facilitates the distribution of Cobalt Strike Beacon on vulnerable devices.
Due to the escalating cyber war, it is crucial for proactive cyber defense measures to be in place. SOC Prime Platform offers cybersecurity professionals advanced and cost-efficient tools to enhance the capabilities of security teams and optimize the ROI of SOC investments.
To help defenders identify possible exploitation attempts related to the CVE-2023-38831 WinRAR flaw in the latest UAC-0057 campaign, SOC Prime’s Threat Detection Marketplace provides a selection of curated Sigma rules. These rules include CTI (Cyber Threat Intelligence) enrichment and are aligned with the MITRE ATT&CK framework. Additionally, they can be used with multiple SIEM, EDR, XDR, and Data Lake formats, with support for automated conversion from Sigma to native technology formats.
To facilitate content search, all the detections are categorized and tagged with relevant identifiers such as “UAC-0057” and “CERT-UA#7435” based on the group and CERT-UA security heads-up identifiers. To access the complete collection of Sigma rules covering the latest UAC-0057 attacks, simply press the “Explore Detections” button on the platform.
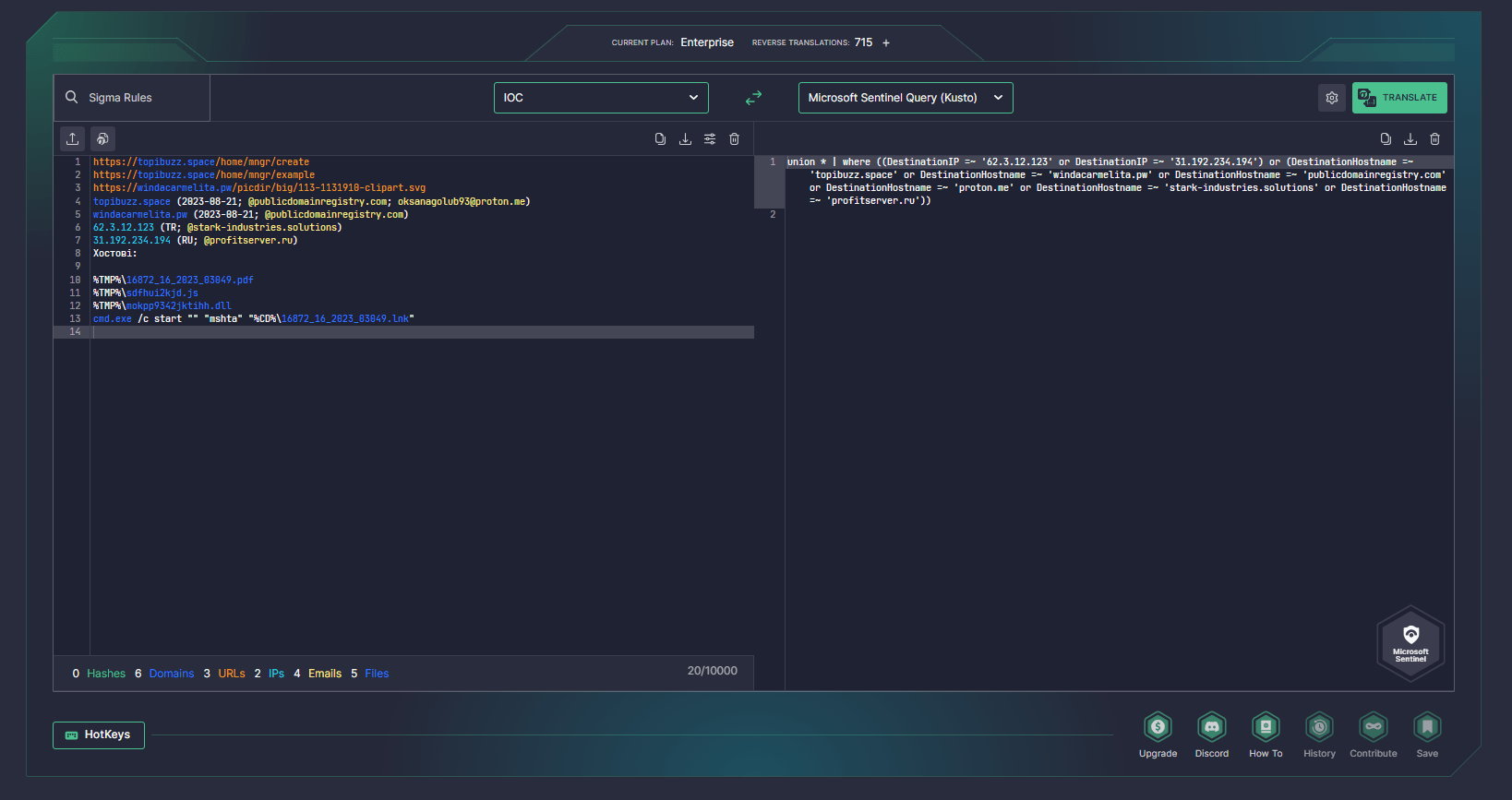
Security professionals can also utilize SOC Prime’s Uncoder AI, an augmented intelligence framework, to expedite threat research. Uncoder AI generates instant IOC (Indicators of Compromise) queries based on the indicators suggested in the latest CERT-UA alert.
Additionally, SOC team members have the opportunity to delve into the attack details outlined in the CERT-UA#7435 alert. The alert provides a comprehensive list of adversary tactics, techniques, and sub-techniques that are applicable to the Sigma rules mentioned earlier, enabling in-depth analysis of the attacks.
In conclusion, the UAC-0057 hacking collective has reemerged, leveraging a zero-day vulnerability in WinRAR to carry out attacks against Ukrainian entities. This serves as a reminder of the importance of proactive cyber defense measures and the availability of advanced tools to detect and mitigate such threats.