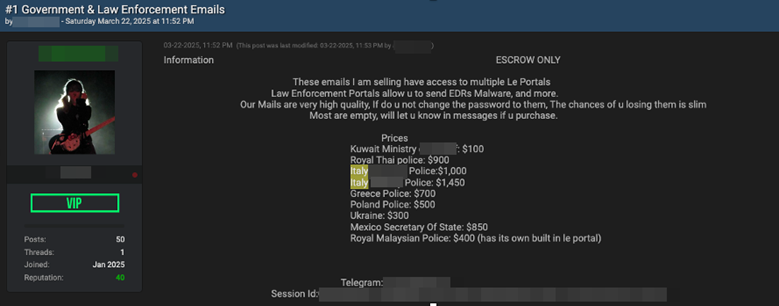
In a new development in the cybercrime landscape, a concerning trend known as “EDR-as-a-Service” has emerged, targeting major platforms with compromised accounts. According to a thorough analysis by the Meridian Group, cybercriminals are utilizing stolen credentials from law enforcement and government agencies to illicitly submit Emergency Data Requests (EDRs) to online platforms. This deceptive tactic allows them to deceive platform operators and gain access to highly sensitive information under the guise of a legitimate investigation.
Initially, criminals were selling stolen credentials, but this illicit market has evolved into a sophisticated “turnkey” model where every aspect of the process is covered. For a fee paid in cryptocurrencies, customers can access the obtained data without requiring technical expertise. The payment mechanisms for such services are handled on Dark Web platforms and underground forums, with transactions typically conducted in Bitcoin or Monero to maintain anonymity.
The professionalization of this illicit sector is evident through the publication of operational manuals and informational content that guide users on how to exploit the obtained data for social engineering and doxxing campaigns. The risks associated with such practices extend beyond individual privacy concerns, with the potential for data to be used in fraudulent schemes, blackmail, or doxing operations targeting high-profile individuals such as activists, journalists, and politicians.
Furthermore, the report highlights a potential interest among ransomware groups in adopting these techniques to enhance their criminal activities. While concrete evidence of this collaboration is yet to be documented, the combination of ransomware attacks with specific data obtained through fraudulent EDRs poses a significant threat to cybersecurity and privacy.
To address this growing issue, the Meridian Group recommends strengthening validation procedures for EDR submissions, including stricter authentication systems for law enforcement requests and enhanced cross-checks by tech companies. Collaboration between authorities and tech companies is essential to prevent the exploitation of institutional channels and protect the privacy of citizens from the evolving tactics of cybercriminals. Failure to address this issue promptly may lead to further organization and commercialization of sensitive information, posing a serious threat to digital security and privacy.
In conclusion, the emergence of “EDR-as-a-Service” highlights the adaptability of cybercriminals in transforming traditional credentials theft into a comprehensive system for accessing sensitive information. Urgent action is required to mitigate the risks posed by this trend and safeguard the integrity of online platforms and the privacy of users. The collaboration between law enforcement agencies, tech companies, and cybersecurity experts is crucial in developing effective countermeasures to address the evolving tactics of cybercriminals in the digital landscape.
For the latest updates on cybersecurity trends and news, follow Pierluigi Paganini on Twitter, Facebook, and Mastodon. Stay informed and stay safe in the ever-evolving cybersecurity landscape.
(Source: SecurityAffairs – hacking, EDR-as-a-Service)