In a groundbreaking development, cybersecurity researchers have successfully identified a critical vulnerability in the encryption process used by Rhysida ransomware, enabling them to recover the encryption key and decrypt data that was previously locked by the malicious software. This revelation was made by a group of researchers from Kookmin University and the Korea Internet and Security Agency (KISA) and marks the first instance of successful decryption of Rhysida ransomware since its emergence in May 2023.
The researchers published their findings last week, detailing the implementation vulnerability that allowed them to regenerate the encryption key used by Rhysida ransomware. They have also announced that a recovery tool is being distributed through KISA, offering much-needed relief to victims of this ransomware attack.
This successful decryption of Rhysida ransomware is the latest in a series of triumphs for cybersecurity researchers who are increasingly leveraging implementation vulnerabilities to neutralize the threat of ransomware attacks. Recent examples include successful data decryption efforts against other ransomware strains such as Magniber v2, Ragnar Locker, Avaddon, and Hive.
Rhysida ransomware, which bears similarities to another ransomware group called Vice Society, is notorious for employing double extortion tactics to pressure victims into making ransom payments by threatening to release their stolen data. The U.S. government issued a warning in November 2023, cautioning various sectors about the potential vulnerability to opportunistic attacks by the threat actors behind Rhysida ransomware.
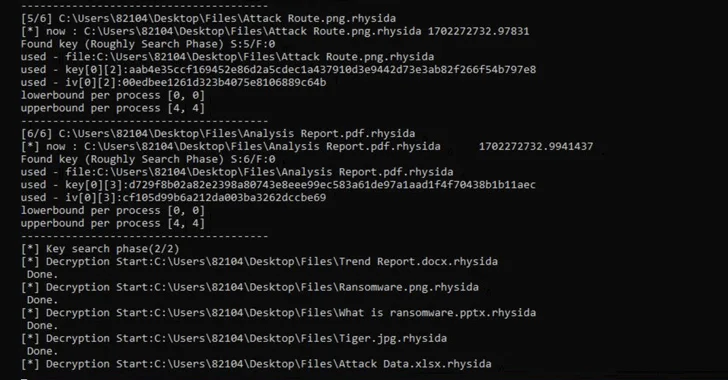
The extensive research into Rhysida ransomware revealed several of the tactics and technologies used by the malware, including its use of LibTomCrypt for encryption and parallel processing to accelerate the encrypting process. Furthermore, it was discovered that the ransomware utilizes a cryptographically secure pseudo-random number generator (CSPRNG) based on the ChaCha20 algorithm provided by the LibTomCrypt library. This generator also correlates the random number generated to the time at which the ransomware is executed, providing valuable insights for researchers seeking to decrypt the data.
Based on these revelations, the researchers were able to retrieve the initial seed for decrypting the ransomware and determine the order in which files were encrypted, ultimately leading to the successful recovery of the data without the need to pay a ransom.
While acknowledging the limited scope of their studies, the researchers emphasized the importance of recognizing that certain ransomware strains can indeed be successfully decrypted, offering a ray of hope to victims of these devastating cyberattacks.
The successful cracking of Rhysida ransomware is a significant milestone in the ongoing battle against ransomware attacks, underscoring the vital role of implementation vulnerabilities in neutralizing these threats. As cybersecurity researchers continue to make strides in unraveling the complex encryption techniques used by ransomware, victims of these attacks can look forward to greater prospects of data recovery without falling victim to extortion demands.
The implications of this breakthrough are far-reaching and are poised to bolster the ongoing efforts to combat ransomware attacks on a global scale. For the latest developments and exclusive content in the field of cybersecurity, stay tuned to our updates on Twitter and LinkedIn.