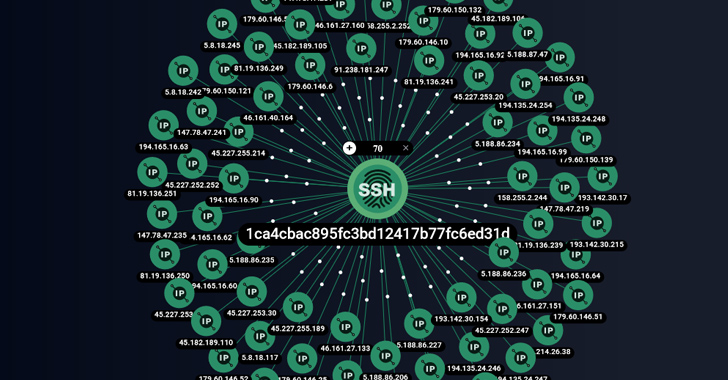
Cybersecurity experts have revealed the existence of a new cybercrime group called ShadowSyndicate, which has been utilizing various ransomware families over the past year. In a joint report by Group-IB and Bridewell, it was stated that ShadowSyndicate works with different ransomware groups and affiliates, and has been active since July 2022. The group has been linked to ransomware activity involving Quantum, Nokoyawa, BlackCat, Royal, Cl0p, Cactus, and Play strains. In addition, ShadowSyndicate has been using off-the-shelf post-exploitation tools like Cobalt Strike and Sliver, as well as loaders such as IcedID and Matanbuchus.
The findings of the report were based on the discovery of a distinct SSH fingerprint on 85 servers, 52 of which were used as command-and-control for the Cobalt Strike tool. Among these servers, eight different Cobalt Strike license keys were found. The majority of the servers were located in Panama, followed by Cyprus, Russia, Seychelles, Costa Rica, Czechia, Belize, Bulgaria, Honduras, and the Netherlands.
Further investigation by Group-IB revealed that ShadowSyndicate is connected to other malware operations, including TrickBot, Ryuk/Conti, FIN7, and TrueBot. According to the report, there have been instances where IP addresses linked to Cl0p ransomware affiliates changed ownership to ShadowSyndicate, indicating a potential sharing of infrastructure between these groups.
The emergence of ShadowSyndicate comes as German law enforcement authorities conducted a second targeted strike against individuals associated with the DoppelPaymer ransomware group. Search warrants were executed against two suspects in Germany and Ukraine, both of whom are alleged to have played key roles in the network and received illicit proceeds from the ransomware attacks.
In a joint advisory, the U.S. Federal Bureau of Investigation (FBI) and the Cybersecurity and Infrastructure Security Agency (CISA) warned about a double extortion actor known as Snatch. This threat actor has been targeting various critical infrastructure sectors since mid-2021 and has been consistently evolving its tactics to evade detection. The agencies highlighted that Snatch primarily relies on exploiting weaknesses in Remote Desktop Protocol (RDP) for brute-forcing and gaining administrator credentials.
The recent report from the U.S. Department of Homeland Security (DHS) further emphasized the continuous development of new methods by ransomware groups to financially extort their victims. The report notes that these groups have increased their use of multilevel extortion, where they encrypt and exfiltrate data, threaten to publicly release stolen data, launch DDoS attacks, or harass the victim’s customers to coerce payment.
One particular ransomware group that has been expanding its reach is Akira. Initially a Windows-based threat, Akira has now extended its capabilities to include Linux servers and VMWare ESXi virtual machines. As of mid-September, the group has successfully attacked 110 victims in the U.S. and the U.K.
The rise in ransomware attacks has also been accompanied by an increase in cyber insurance claims. According to cyber insurance firm Coalition, overall claims frequency in the first half of the year in the U.S. has increased by 12%. Victims have reported an average loss amount of over $365,000, a significant jump from the second half of 2022.
The threat landscape continues to evolve, with ransomware families like BlackCat, Cl0p, and LockBit remaining prolific and adaptive. These ransomware groups have been targeting small and large enterprises across various sectors such as banking, retail, and transportation. The number of active Ransomware as a Service (RaaS) and RaaS-related groups has also grown, indicating the expanding threat landscape.
Recent attacks by LockBit have highlighted the group’s use of internet-exposed remote monitoring and management (RMM) tools to spread ransomware within victim companies’ IT environments. This technique, known as living-off-the-land (LotL), aims to evade detection by blending malicious activity with legitimate use of IT management tools. Similarly, a BlackCat attack observed by Sophos involved the encryption of Microsoft Azure Storage accounts after the attackers gained access to a customer’s Azure portal.
It is clear that ransomware groups are continuously evolving their tactics and targeting a wide range of sectors. As a result, cybersecurity professionals and law enforcement agencies must remain vigilant and proactive in their efforts to detect and prevent these attacks.