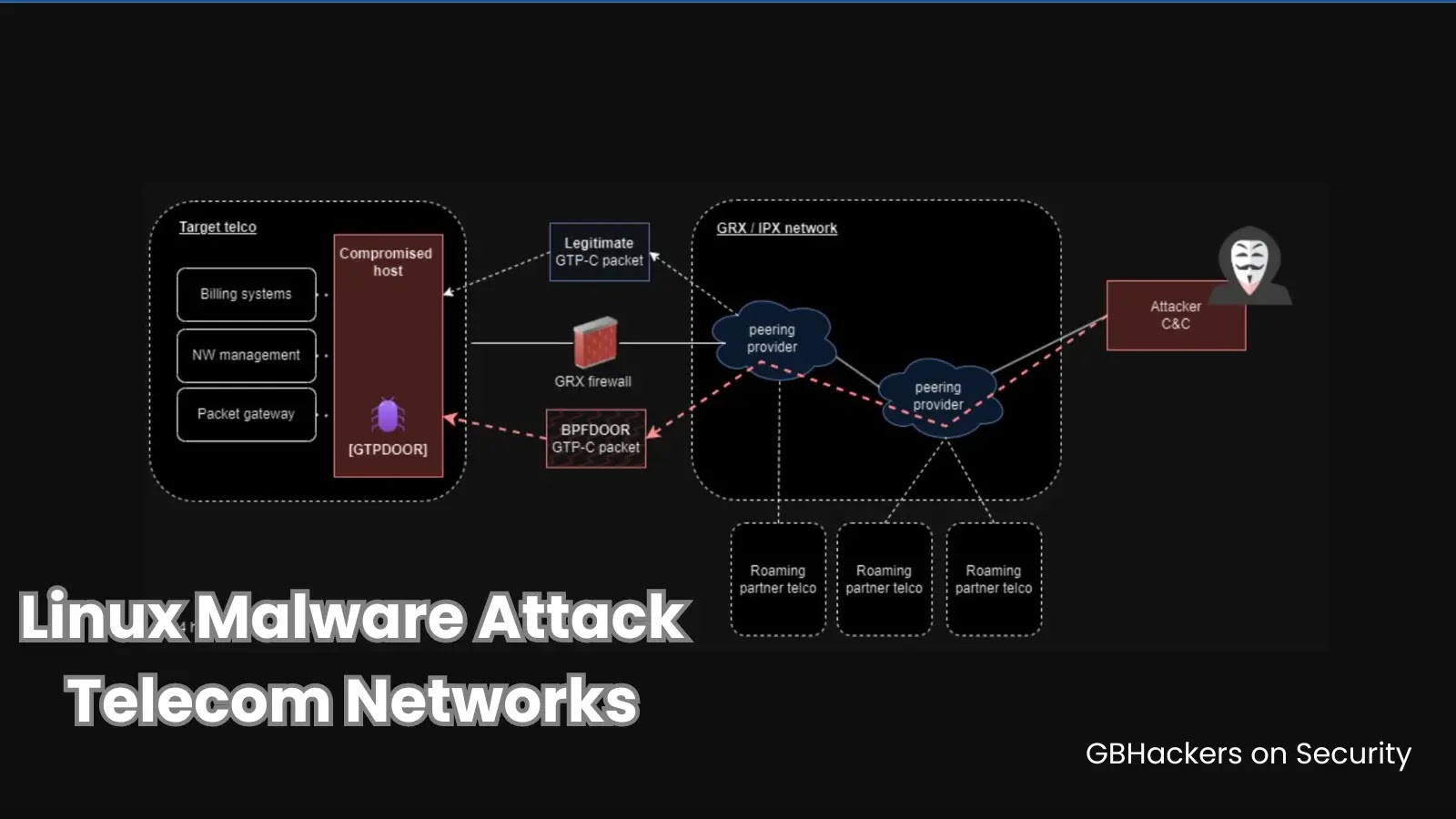
Researchers have unveiled a new backdoor known as GTPDOOR that specifically targets telecommunication network systems operating within the GRX network, a closed system that links multiple telecom operators. These operators rely on network elements such as SGSN, GGSN, P-GW, STP, and DRA to establish direct connections to the GRX network for routing roaming traffic, which utilizes the GTP-C protocol for communication.
GTPDOOR has been strategically designed to operate covertly and remain undetected by leveraging the GTP-C protocol, a legitimate protocol commonly used for communication within mobile networks. By camouflaging itself within regular traffic, GTPDOOR aims to avoid detection and maintain its stealth. Moreover, the backdoor can modify its process name to imitate legitimate system processes, further enhancing its ability to evade detection by security measures.
According to observations made by Double Agent, GTPDOOR establishes communication with a command and control server using the GTP-C protocol. This enables the malware to receive commands from malicious actors and transmit any stolen data or acquired information back to the attackers.
GTPDOOR, a Linux-based malware, operates by sending “magic” packets, specifically GTP-C echo requests, to activate infected systems, execute commands sent by the attackers, and return the results. Remote probing, process name alteration for evading detection, and XOR encryption for authentication and support key changes are all utilized by this malicious software. Its deployment of established protocols and ports within authentic network traffic further complicates the identification process, making it challenging to detect and mitigate the threat.
An in-depth analysis of GTPDOOR has revealed the presence of two malicious samples, pickup (the enhanced version) and dbus-echo, targeting an outdated Linux system (RHEL 5.x). The source code of these samples indicates inadequate maintenance by the attacker. The discovery of these samples on VirusTotal in late 2023 underscores the ongoing threat posed by such malware within telecommunication networks.
GTPDOOR’s operations involve the use of GTP Echo Request messages for concealed communication, listening for UDP packets specifically on port 2123, message authentication using a hardcoded key, and payload decryption. Different message types trigger various actions, such as executing shell commands, modifying the Access Control List, retrieving the current ACL, or clearing the ACL.
Furthermore, an enhanced version of GTPDOOR, known as GTPDOOR v2, introduces additional functionalities such as multithreading for handling GTP and TCP communication, conducting liveness checks through specific TCP packet responses, and forking processes to execute remote commands using open().
In light of these developments, system administrators are encouraged to utilize tools like “lsof” and “netstat” to examine raw sockets for suspicious entries. Anomalies like malformed GTP packets, processes with abnormal parent IDs, and specific file presence could indicate a GTPDOOR infection, necessitating quick detection and mitigation efforts.
Network traffic analysis, coupled with properly configured firewalls and adherence to industry guidelines released by organizations like GSMA, can help identify and mitigate the threat posed by GTPDOOR and similar malware. By taking proactive measures and implementing robust security protocols, organizations can bolster their defenses against emerging cyber threats targeting critical telecommunication infrastructure.