Evasive Panda, a known cyber espionage group associated with China, has been using a sophisticated toolset called CloudScout to target government entities and religious organizations in Taiwan. This toolset, which was active between 2022 and 2023, is designed to steal data from various cloud services by utilizing stolen web session cookies. The CloudScout toolset works in conjunction with MgBot, Evasive Panda’s malware framework, to seamlessly carry out its operations.
One of the key features of CloudScout is its ability to access and exfiltrate data from popular cloud services such as Google Drive, Gmail, and Outlook by leveraging stolen cookies provided by MgBot plugins. Through our analysis, we have identified three CloudScout modules dedicated to stealing data from these specific cloud services. However, we suspect that there are at least seven additional modules that have yet to be observed in the wild.
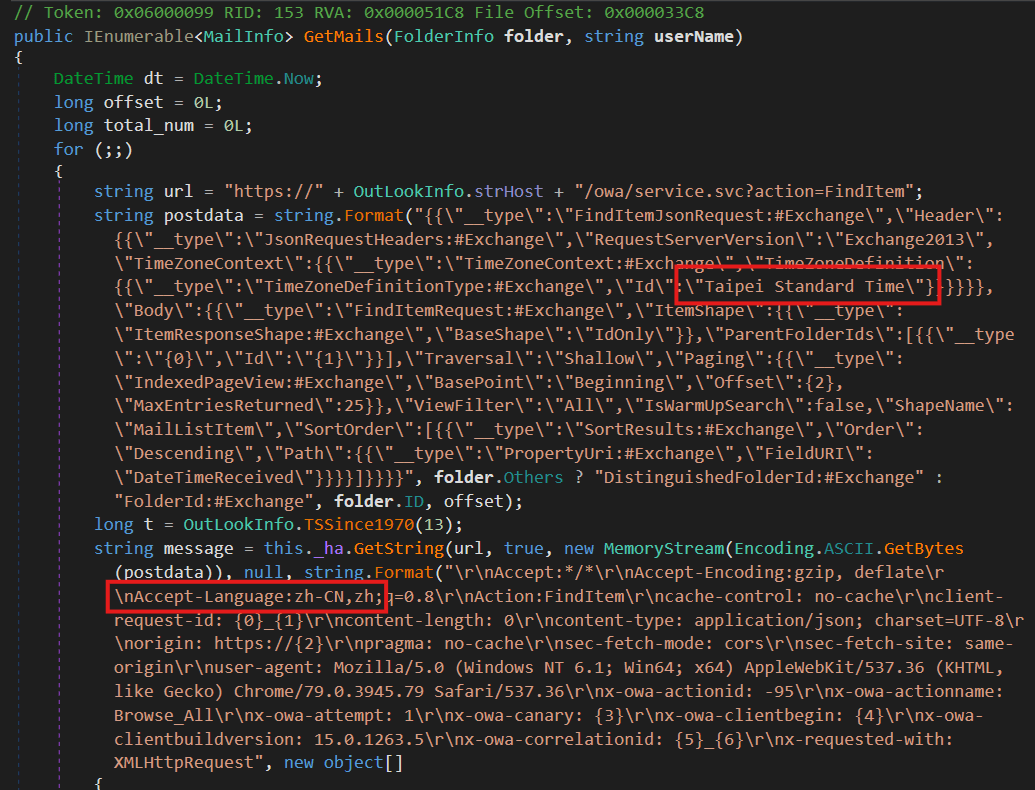
In our examination of the CloudScout modules, we found hardcoded fields in the web requests for stealing Outlook email messages, indicating that the samples were specifically crafted to target Taiwanese users. The modules, written in C#, are deployed by MgBot plugins written in C++, further showcasing the advanced capabilities of Evasive Panda in conducting cyber espionage operations.
Evasive Panda, also known by aliases such as BRONZE HIGHLAND, Daggerfly, or StormBamboo, has a long history of targeting organizations and countries that oppose Chinese interests. Their cyberespionage activities have extended beyond Taiwan to countries like Vietnam, Myanmar, and South Korea. The group has shown proficiency in using sophisticated techniques such as supply-chain and watering-hole attacks, as well as taking advantage of vulnerabilities in software like Microsoft Office and web servers.
The CloudScout toolset was first detected in Taiwan in early 2023, where three previously unknown .NET modules were deployed at a government entity. These modules were designed to hijack authenticated web sessions and access data stored in public cloud services. However, with the release of protective measures like Device Bound Session Credentials by Google in 2023 and App-Bound Encryption by Chrome in 2024, tools like CloudScout may become obsolete in the near future.
Further analysis of the CloudScout modules revealed a consistent development framework codenamed CloudScout, indicating a structured approach to building and deploying this toolset. The modules share a common architecture and design, with each module tailored to target specific cloud services and extract valuable data for exfiltration.
Despite the intricacies of the CloudScout toolset, Evasive Panda’s operations demonstrate a relentless pursuit of acquiring sensitive information from targeted entities. By utilizing stolen cookies and sophisticated malware frameworks, the group has been able to infiltrate organizations and governments to further their espionage goals.
The technical analysis conducted on the CloudScout toolset sheds light on the advanced capabilities of Evasive Panda and underscores the importance of safeguarding cloud services from such cyber threats. As new protective measures are introduced to mitigate cookie-theft malware, organizations and governments must remain vigilant in defending against cyber attacks from sophisticated threat actors like Evasive Panda.