In a recent discovery by cybersecurity researchers at CloudSec, a new phishing campaign has been identified targeting Windows users. This campaign utilizes fake CAPTCHA verification pages to deceive users into running malicious PowerShell commands, ultimately leading to the installation of the Lumma Stealer malware and the theft of sensitive information.
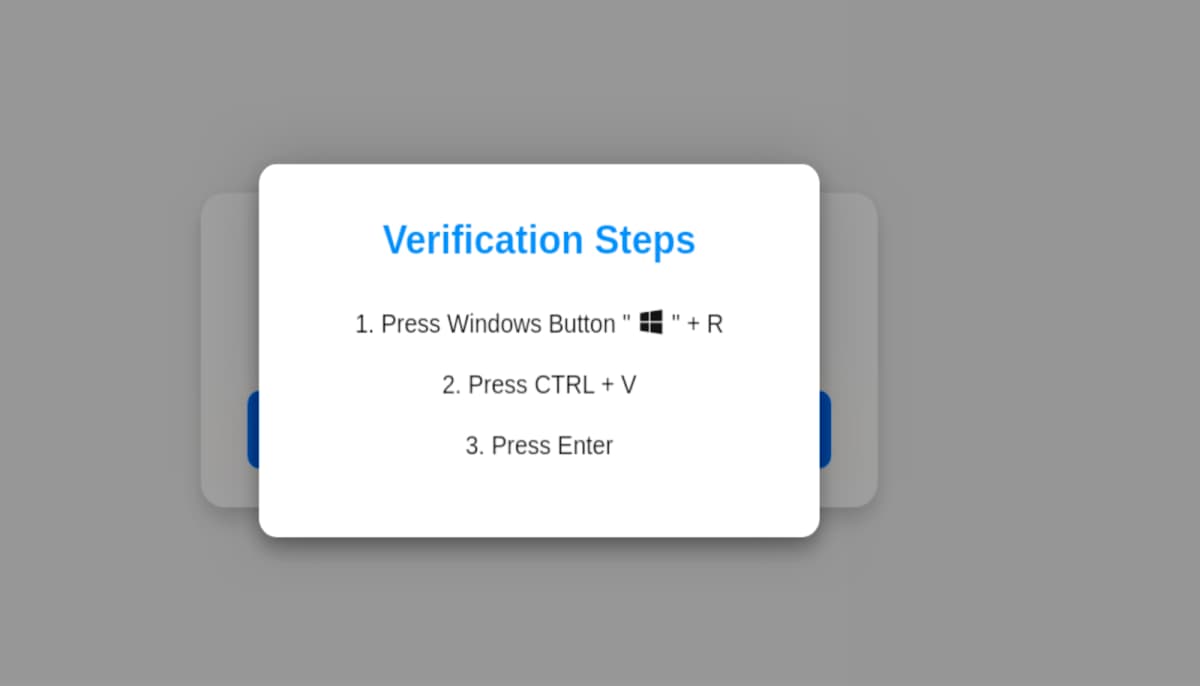
The modus operandi of this attack involves threat actors creating phishing sites hosted on various platforms, including Amazon S3 buckets and Content Delivery Networks (CDNs). These sites impersonate legitimate verification pages, such as fake Google CAPTCHA pages. When unsuspecting users click the “Verify” button on these fake pages, they are presented with peculiar instructions to open the Run dialog (Win+R), press Ctrl+V, and hit Enter. Little do they know, these actions trigger a hidden JavaScript function that copies a base64-encoded PowerShell command to the clipboard. Upon pasting and executing this command, the Lumma Stealer malware is downloaded from a remote server.
According to CloudSec’s report, the downloaded malware often fetches additional malicious components, complicating detection and removal processes. While the current use of this technique is to distribute Lumma Stealer, it can easily be adapted to disseminate other forms of malware, posing a significant threat to cybersecurity.
The Lumma Stealer malware itself is designed to pilfer sensitive data from infected devices, including login credentials, financial information, and personal files. This latest phishing campaign comes hot on the heels of a previous incident where the malware masqueraded as an OnlyFans hacker tool, infecting the devices of unsuspecting users.
Previously, Lumma Stealer was found spreading through cracked software distributed via compromised YouTube channels in January 2024. In November 2023, researchers uncovered a new version of the malware, LummaC2 v4.0, which utilized trigonometric techniques to detect human users and steal their data.
In light of this new Lumma Stealer infection spree, it is imperative for businesses and individuals to remain vigilant and guard against falling prey to this latest fake verification scam. Simple yet essential tips for protection include educating oneself and others about the threat, being cautious of unusual verification requests, refraining from copying and pasting unknown commands, keeping software updated, and staying informed with the latest cybersecurity news from trusted sources like Hackread.com.
As cyber threats continue to evolve and become more sophisticated, it is crucial for users to be proactive in safeguarding their digital assets and personal information. By staying informed, adopting best practices for online security, and remaining vigilant against phishing attempts, individuals can reduce their risk of falling victim to malicious actors seeking to exploit vulnerabilities for their gain.