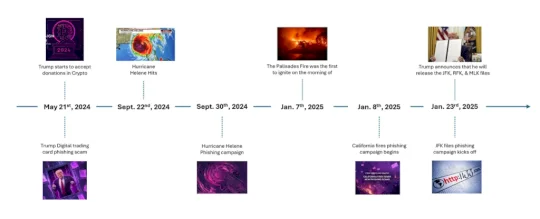
Veriti Research recently uncovered a concerning cyber threat campaign related to the release of the declassified JFK, RFK, and MLK files. Cyber attackers are taking advantage of the public interest in these historical documents to launch potential malware campaigns, phishing schemes, and exploit attempts. The swift response of cybercriminals following major public events like this is a troubling trend that Veriti Research has been monitoring closely.
As these declassified files gain media attention, attackers are already setting up infrastructure for their upcoming attacks. Within days of the announcement regarding the release of the JFK-related files, several suspicious domains were registered with the intention of impersonating legitimate sources. This indicates that cybercriminals are proactive in exploiting any significant event to carry out their malicious activities.
Some of the suspicious domains that have been identified include Thejfkfiles[.]com, jfk-files[.]com, rfkfiles[.]com, and jfk-files[.]org. These domains could potentially be used for phishing attacks, malware distribution, or social engineering tactics aimed at stealing sensitive information from unsuspecting users.
Veriti Research has identified key attack vectors that cybercriminals may use to target individuals seeking access to the declassified files. These include embedding malware into files labeled as official document releases, creating fake phishing websites that mimic official sources, exploiting browser vulnerabilities, and sending phishing emails posing as credible sources offering exclusive access to the files. All these techniques are designed to trick users into downloading malicious content or providing personal information.
Events of historical and public importance have always been attractive targets for cyber attackers looking to exploit vulnerabilities. Similar trends have been observed with past global events, such as COVID-19 scams, election-related campaigns, and cryptocurrency frauds. The upcoming attacks leveraging the JFK files underscore the importance of maintaining cyber resilience in the face of social engineering tactics.
It is crucial for individuals and organizations to verify the authenticity of sources before downloading any files related to the declassified JFK documents. Official government websites like the National Archives should be the primary source for accessing such sensitive information. It is advisable to avoid downloading files from unknown third-party websites or clicking on suspicious links shared on social media platforms.
The exploitation of the JFK files serves as a reminder of the agility and adaptability of cybercriminals in exploiting real-world events for their malicious activities. Veriti Research will continue to monitor the evolving cyber threats surrounding the release of these historical documents and provide updates on new attack methods. Staying informed, exercising caution, and spreading cybersecurity awareness within your organization and network are essential steps to protect against such cyber threats.
In conclusion, the cybersecurity landscape is constantly evolving, and individuals must remain vigilant to safeguard themselves against potential cyber attacks.