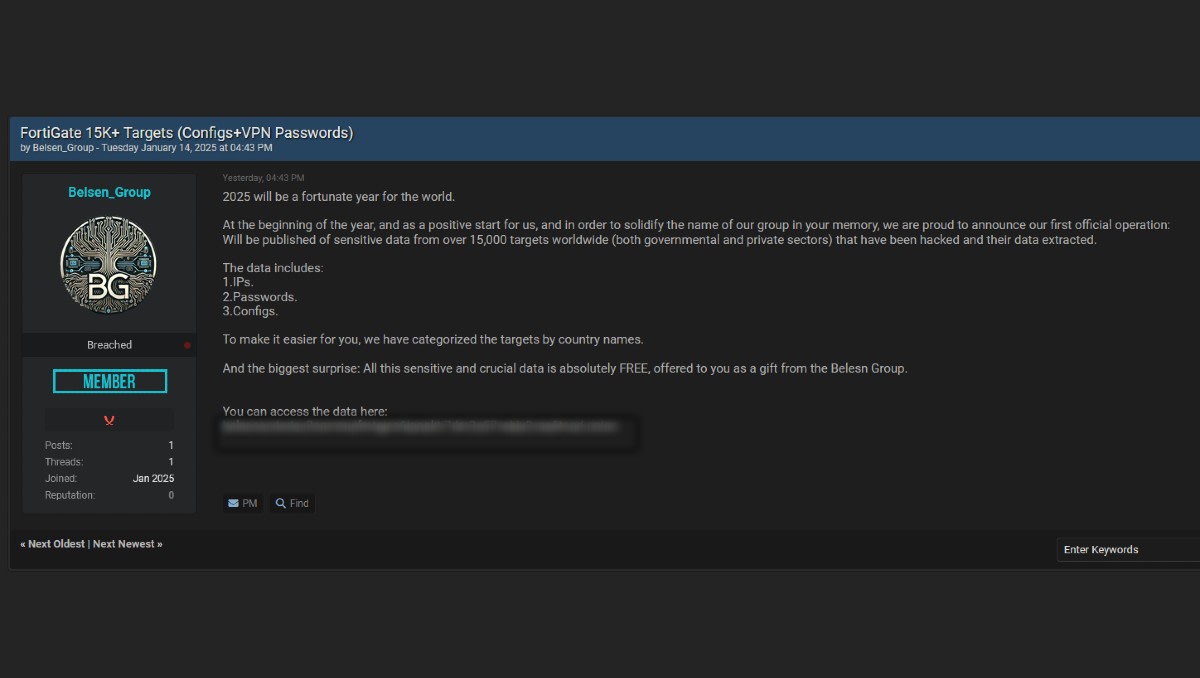
A recent development in the ongoing cybersecurity saga involving vulnerable Fortinet FortiGate firewall devices has brought a new hacking group into the spotlight. The Belsen Group, a newcomer to the hacking scene, made a grand entrance by sharing the keys to more than 15,000 vulnerable devices on a popular hacking forum. This data, which includes IP addresses, passwords, and full configuration details, poses a significant threat to both governmental and private sectors worldwide.
The Belsen Group’s post on 14 January hinted at their ambitious plans for the future, proclaiming that “2025 will be a fortunate year for the world.” They proudly announced their first official operation, which involved the release of sensitive data extracted from over 15,000 targets. The 1.6-gigabyte .ZIP archive containing this data is hosted on the group’s darknet site, offered as a gift to the public free of charge.
Cybersecurity specialist Kevin Beaumont confirmed the legitimacy of the data, noting that the FortiGate configurations appear to be authentic and unique. He raised concerns about a possible zero-day vulnerability in Fortinet’s devices, hinting that the recently disclosed CVE may not cover the full extent of the issue. Further investigations revealed that the files relate to an earlier CVE, CVE-2022–40684, indicating that the data was compiled in October 2022 as a zero-day exploit.
Beaumont’s analysis highlighted the potential risks posed by the leaked data, emphasizing the importance of patching vulnerabilities promptly. He advised organizations to assess their patching history to determine if they may have been compromised by the exploit. The timing of the Belsen Group’s data dump coincides with Fortinet’s recent disclosure of CVE-2024-55591, suggesting a strategic attempt to exploit the latest vulnerability in FortiGate devices.
Fortinet’s response to the security concerns includes mitigation advice to address the Authentication Bypass Vulnerability affecting FortiOS and FortiProxy. The company urged users to update their FortiGuard appliances and restrict access to the administrative interface to prevent unauthorized exploitation. Reports indicate that the vulnerability is actively being exploited in the wild, underscoring the urgency for users to secure their devices promptly.
As the cybersecurity landscape continues to evolve, the emergence of new threat actors like the Belsen Group highlights the need for organizations to remain vigilant and proactive in their cybersecurity practices. The rapid pace of cyber threats underscores the importance of timely patching, monitoring, and response strategies to protect against potential breaches and data leaks. Stay tuned for further updates on this developing cybersecurity incident.