Attacks on industrial control systems and operations technology systems are on the rise, with cyber adversaries exploiting vulnerabilities in IT networks to infiltrate OT networks, as revealed in a recent report published by SANS.
Based on input from cybersecurity experts across critical infrastructure sectors, the State of ICS/OT Cybersecurity 2024 report underscores a concerning trend. The findings show that there have been more non-ransomware incidents (74.4%) compared to ransomware attacks (11.7%) over the past year.
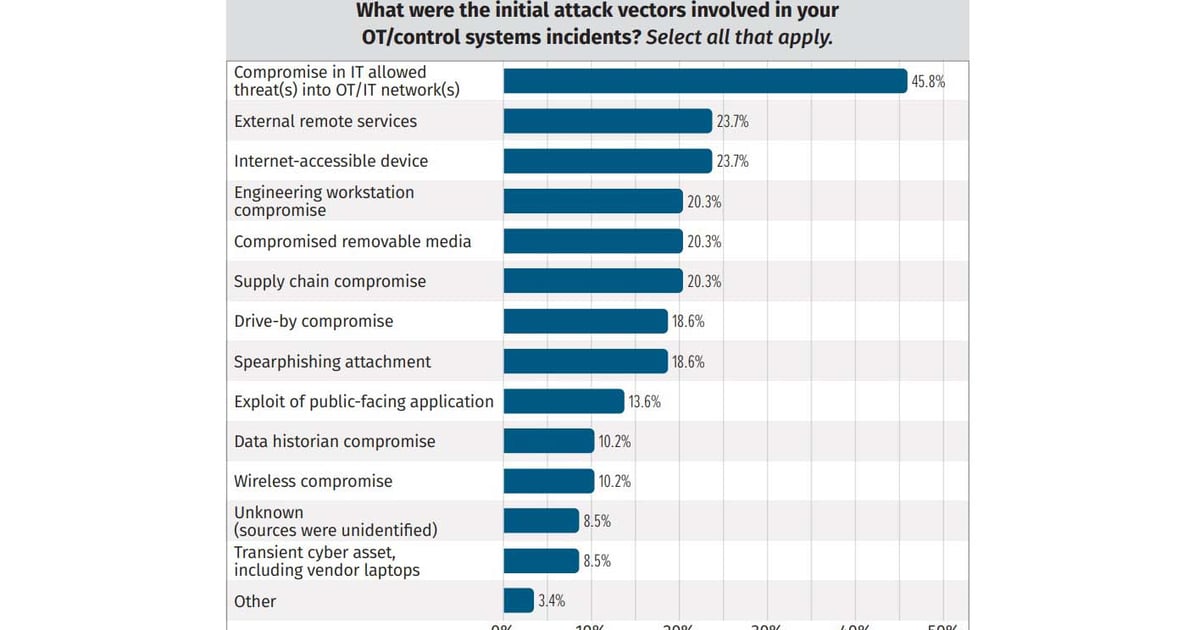
Various initial attack vectors were identified in OT/ICS incidents, including the compromise of OT and industrial control systems through external remote services (23.7%) or internet-accessible devices (23.7%). Additionally, attacks were carried out via employee workstations (20.3%), removable media (20.3%), and supply chain compromises (20.3%). Alarmingly, 18.6% of respondents reported attackers resorting to spear phishing with email attachments for the initial breach.
Interestingly, 19% of respondents reported experiencing one or more security incidents within the past year, indicating the widespread nature of cyber threats targeting industrial systems.
Even though only 12% of respondents reported being victims of ransomware attacks in the previous 12 months, the impact on ICS/OT environments is described as “potentially catastrophic” by SANS. Among the organizations affected by ransomware, 38% reported impacts limited to IT network systems, while 28.6% said their OT and ICS networks were compromised. A smaller percentage, 21%, noted impacts on both networks. Moreover, 38.1% stated that reliability and safety were compromised during these attacks.
SANS emphasized the severity of ransomware attacks, noting that while the overall trend may be decreasing, the potential consequences remain significant and should be a key consideration for all incident response programs tailored to ICS/OT environments.
The escalating threat landscape targeting industrial systems underscores the need for robust cybersecurity measures and proactive defenses to safeguard critical infrastructure. As cyber adversaries continue to evolve their tactics, organizations must prioritize cybersecurity readiness and resilience to mitigate the impact of cyber attacks on industrial control systems and operations technology.