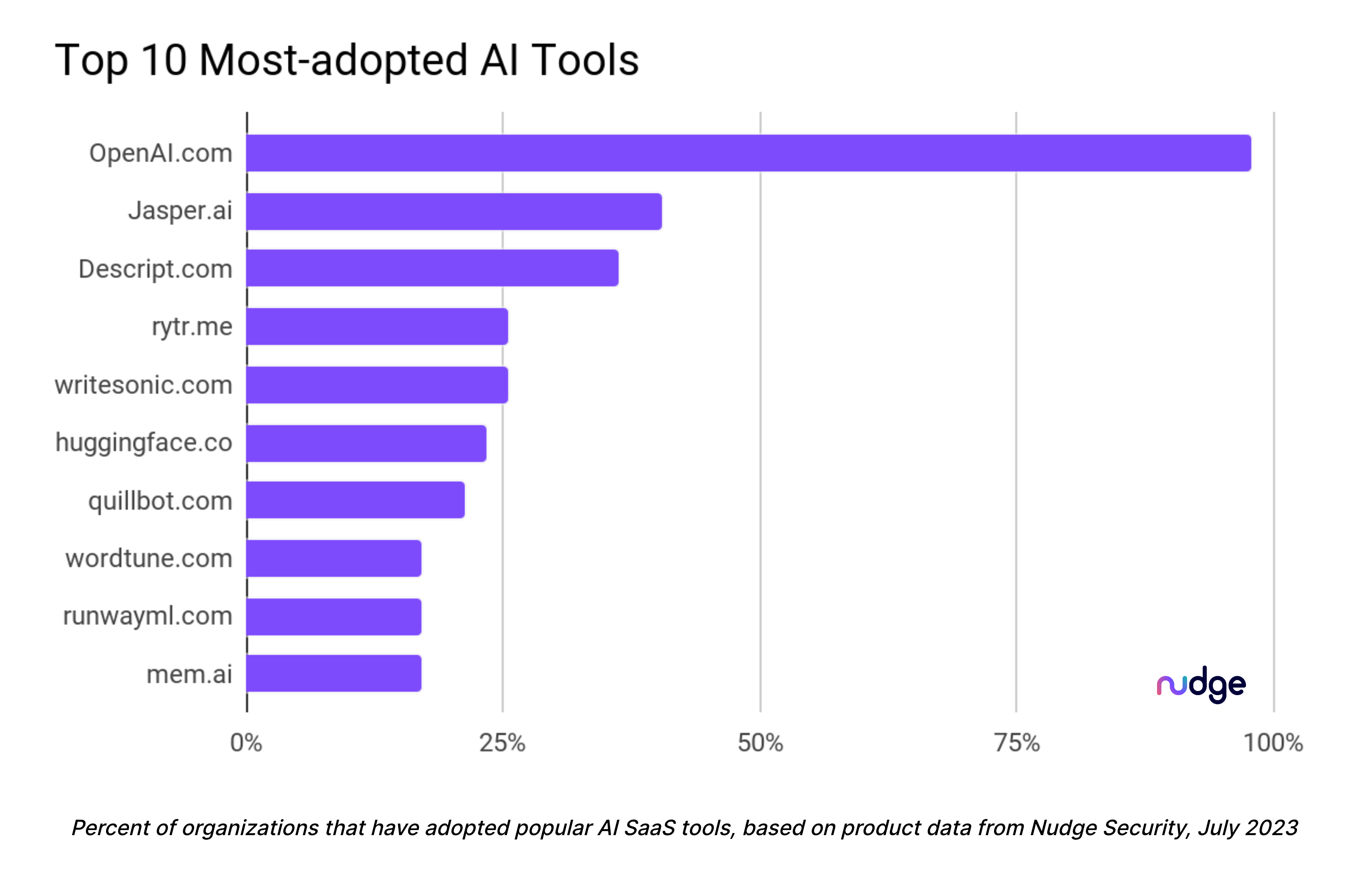
In today’s rapidly evolving marketplace, artificial intelligence (AI) tools are becoming increasingly prevalent. With numerous new AI tools entering the market and existing tools enhancing their features with AI capabilities, organizations are struggling to keep track of which tools are being used, how they are used, who has access to them, and what data is being shared. According to data from Nudge Security, on average, organizations are utilizing six AI tools, with ChatGPT and Jasper.ai being the most widely adopted.
As businesses experiment with various generative AI tools, IT, risk, and security leaders are faced with the challenge of governing and securing their use while still fostering innovation. Establishing robust security policies to oversee AI usage is crucial; however, implementing such policies becomes impossible without having a clear understanding of the tools in use.
The adoption of ChatGPT, provided by OpenAI.com, is particularly noteworthy, as illustrated in the accompanying chart. Yet, there are several other AI tools vying for attention in the market. While some may not be as familiar as ChatGPT, such as rytr.me and wordtune.com, security teams must still become acquainted with these tools and develop policies governing their usage. Another well-known AI tool, Huggingface.co, falls squarely in the middle of the pack in terms of adoption rate.
When addressing the utilization of generative AI tools within an enterprise setting, security teams need to consider the discovery process—identifying which tools have been introduced into the environment and by whom. Additionally, conducting thorough risk assessments involves examining the security and risk profiles of the AI vendors. Equally important is ensuring that business users who create experimental accounts for testing purposes deactivate these accounts properly if they are no longer needed.
By effectively managing these aspects of AI tool usage, organizations can balance innovation and security, benefiting from the advantages that AI offers without compromising their cybersecurity posture. However, gaining visibility into the deployment and usage of AI tools remains a crucial first step in achieving this balance.
In the ever-evolving landscape of cybersecurity, it is essential for organizations to stay updated on the latest threats, vulnerabilities, data breaches, and emerging trends. To help with this, Dark Reading offers a daily or weekly email newsletter, delivering the most pertinent cybersecurity information directly to subscribers’ inboxes. This resource is valuable to both individuals and organizations seeking to stay informed and enhance their security measures.
In conclusion, as AI tools continue to proliferate, organizations face the challenge of managing their usage effectively. Achieving this requires visibility into the AI tools being deployed, their usage patterns, and the associated risks. By understanding which tools are in use, organizations can develop robust security policies to govern their usage while still driving innovation. Moreover, maintaining a proactive approach to account management and deactivation ensures that organizations can minimize the potential risks associated with abandoned accounts. With a careful balance between innovation and security, organizations can harness the power of AI tools while safeguarding their valuable data and systems from cyber threats.