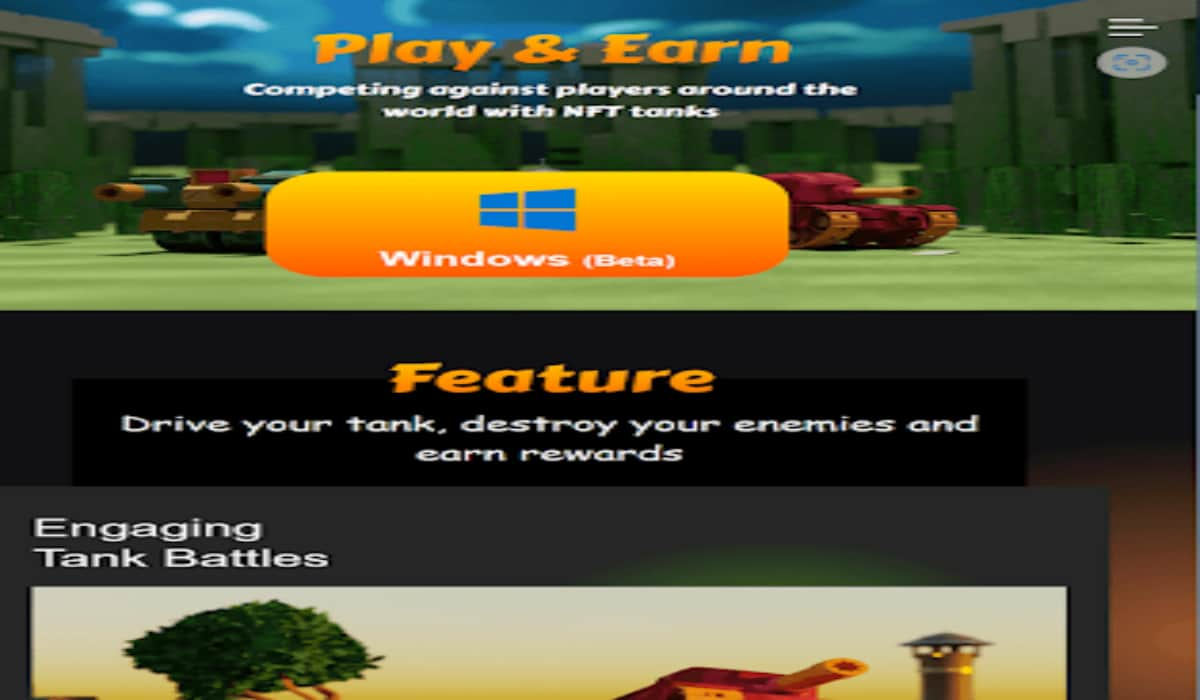
North Korean hackers from the Lazarus Group have once again made headlines for their latest cyberattack targeting cryptocurrency investors. The sophisticated attack campaign involved exploiting a zero-day vulnerability in Google Chrome to deceive unsuspecting victims with a fake NFT game called “DeFiTankZone.”
Kaspersky researchers uncovered this elaborate scheme in May 2024 when they detected the use of the Manuscrypt backdoor to target a Russian individual’s personal computer. The attack chain, which started in February 2024, was orchestrated by the Lazarus Group through a deceptive website named “detankzonecom.” This website masqueraded as a platform for the fictional DeFiTankZone game, combining elements of Decentralized Finance (DeFi) and Non-Fungible Tokens (NFTs) in a MOBA setting.
The fake game website lured victims in with promises of an exciting gaming experience, complete with a downloadable trial version. However, beneath its enticing facade, the website harbored a malicious script designed to exploit a zero-day vulnerability in Google Chrome. This exploit, which enabled the attackers to take full control of the victim’s PC, relied on two vulnerabilities in the Chrome process, including CVE-2024-4947, a type confusion bug in the V8 JavaScript and WebAssembly engine.
Once the attackers gained access to the victims’ devices, they deployed a custom script to gather valuable information and assess the potential for further exploitation. The specific payload delivered at this stage remains undisclosed, leaving experts concerned about the extent of the damage caused by the cybercriminals.
In their bid to target influential figures in the cryptocurrency space, the Lazarus Group utilized social media platforms like X (formerly Twitter) and LinkedIn. By creating a compelling online presence for the fake game and leveraging generative AI and graphic designers to produce high-quality promotional material, the attackers sought to entice their targets into falling for their ploy. Additionally, the group sent tailored emails to individuals, posing as blockchain companies or game developers offering investment opportunities.
The DeTankZone website’s origins trace back to the stolen source code of a legitimate blockchain game called DeFiTankLand (DFTL), which suffered a security breach in March 2024 resulting in the theft of $20,000 worth of cryptocurrency. While the original developers suspected an insider, Kaspersky researchers now believe that the Lazarus Group could be behind both the theft and the repurposing of the stolen source code for their malicious campaign.
This incident underscores the evolving strategies employed by the Lazarus Group and serves as a cautionary tale for individuals involved in the cryptocurrency industry. Vigilance against unsolicited investment offers, particularly those involving downloadable game clients or suspicious social media promotions, is crucial in safeguarding against cyber threats. Furthermore, maintaining up-to-date browser software with the latest security patches is essential to mitigate the risk of zero-day exploits.
As the cybersecurity landscape continues to evolve, staying informed about the tactics used by threat actors like the Lazarus Group is imperative for enhancing overall digital defense strategies. By remaining vigilant and proactive in cybersecurity practices, individuals and organizations can better protect themselves against sophisticated cyber threats in an increasingly interconnected world.