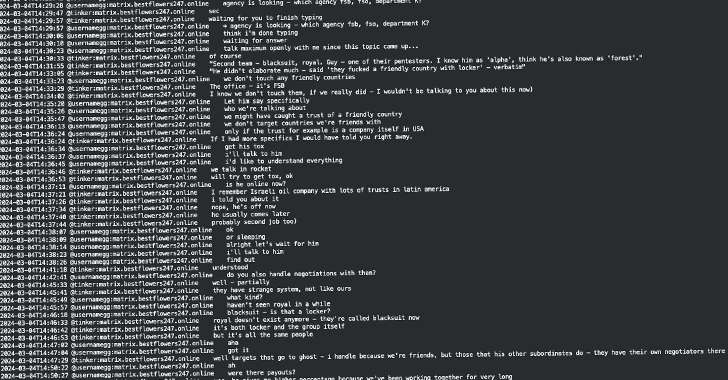
A recent leak of internal chat logs from the Black Basta ransomware operation has shed light on potential connections between the cybercriminal group and Russian authorities. The leak, which contained more than 200,000 messages spanning from September 2023 to September 2024, was made public by a Telegram user known as @ExploitWhispers last month.
According to an analysis conducted by cybersecurity firm Trellix, the leader of Black Basta, Oleg Nefedov (also known as GG or AA), may have received assistance from Russian officials following his arrest in Yerevan, Armenia in June 2024. This aid allegedly allowed him to escape custody three days later. In the leaked messages, GG mentioned contacting high-ranking officials to secure a “green corridor” for his escape.
The revelation of these details has posed challenges for the Black Basta gang, as it implies that they may struggle to completely overhaul their operations and establish a new Ransomware-as-a-Service (RaaS) model without ties to their past activities. Trellix researchers Jambul Tologonov and John Fokker highlighted the implications of this information, emphasizing the difficulty the group may face in distancing themselves from their previous modus operandi.
Among the key findings from the leaked chat logs are:
– The potential presence of two Black Basta offices in Moscow
– The use of OpenAI ChatGPT for various nefarious purposes, including writing fraudulent letters, debugging code, and collecting victim data
– Overlapping members with other ransomware groups like Rhysida and CACTUS
– Collaboration with a Ukrainian developer known as mecor on developing new ransomware derived from Conti’s source code
Additionally, the leak revealed that Black Basta rented DarkGate from a group called Rastafareye and employed Lumma Stealer to steal credentials and distribute additional malware. The group also created a post-exploitation command-and-control (C2) framework named Breaker to facilitate persistence, evade detection, and maintain access to network systems.
Moreover, the leaked messages exposed Black Basta’s involvement in developing a brute-forcing framework called BRUTED, designed to automate internet scanning and credential stuffing attacks on edge network devices, such as firewalls and VPN solutions. This tool has allowed the group to expand their victim pool and expedite ransomware operations.
The use of the PHP-based BRUTED framework since 2023 has enabled Black Basta affiliates to conduct large-scale attacks on target devices, providing them with crucial insights into victim networks. Security researcher Arda Büyükkaya emphasized the significance of the framework in enabling the group to automate and scale their attacks, ultimately driving their illicit operations.
In conclusion, the leaked chat logs have provided valuable insights into the inner workings of the Black Basta ransomware operation, revealing potential ties to Russian authorities and shedding light on the group’s extensive cybercriminal activities. The implications of these revelations underscore the complex and interconnected nature of the cybercrime landscape, highlighting the ongoing challenges faced by law enforcement and cybersecurity professionals in combating such threats.