An updated version of a malware loader known as BLISTER is being used as part of SocGholish infection chains to distribute an open-source command-and-control (C2) framework called Mythic.
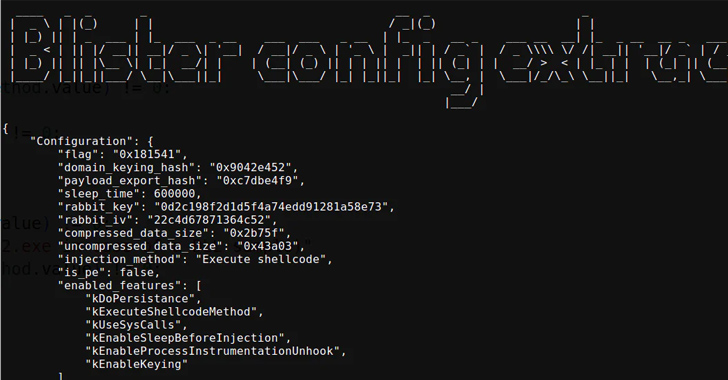
“New BLISTER update includes keying feature that allows for precise targeting of victim networks and lowers exposure within VM/sandbox environments,” Elastic Security Labs researchers Salim Bitam and Daniel Stepanic said in a technical report published late last month.
BLISTER was first uncovered by the company in December 2021 acting as a conduit to distribute Cobalt Strike and BitRAT payloads on compromised systems.
The use of the malware alongside SocGholish (aka FakeUpdates), a JavaScript-based downloader malware, to deliver Mythic was previously disclosed by Palo Alto Networks Unit 42 in July 2023.
In these attacks, BLISTER is embedded within a legitimate VLC Media Player library in an attempt to get around security software and infiltrate victim environments.
Both SocGholish and BLISTER have been used in tandem as part of several campaigns, with the latter used as a second-stage loader to distribute Cobalt Strike and LockBit ransomware, as evidenced by Red Canary and Trend Micro in early 2022.
A closer analysis of the malware shows that it’s being actively maintained, with the malware authors incorporating a slew of techniques to fly under the radar and complicate analysis.
“BLISTER is a loader that continues to stay under the radar, actively being used to load a variety of malware including clipbankers, information stealers, trojans, ransomware, and shellcode,” Elastic noted in April 2023.
-REFERENCE: https://thehackernews.com/2023/09/new-blister-malware-update-fuelling.html
-K.Z