Concerns are mounting as organizations increasingly rely on cloud services, mobile devices, and digital technologies to cater to customer demands and support remote workforces. In this paradigm, identity has become the new security perimeter, encompassing the authentication, authorization, and management of users, applications, and devices. To bolster this crucial defense line, investments in identity technologies like single sign-on, multifactor authentication, continuous monitoring, and identity access management are imperative.
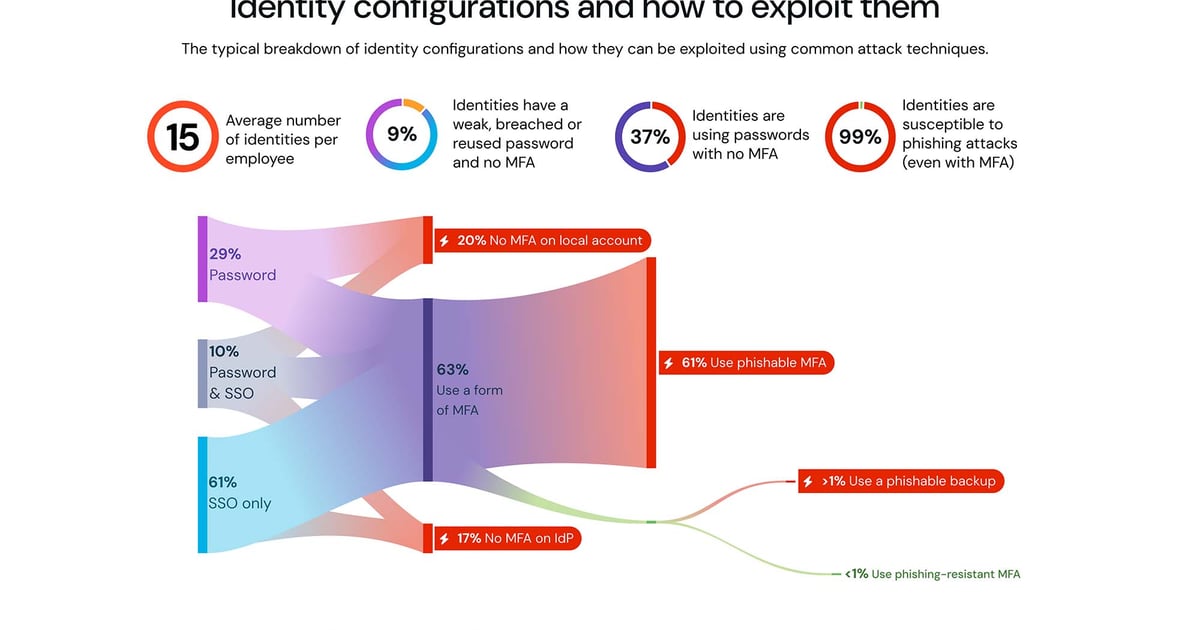
The vulnerability of organizations to identity-based attacks, such as credential stuffing, brute-force, and phishing, has been underscored by a recent analysis conducted by Push Security’s research team. The study, which scrutinized 300,000 accounts and associated login methods, revealed that the average employee in a typical organization has 15 identities. Alarmingly, 37% of these identities utilized password-based logins without multifactor authentication (MFA).
Further insights from the analysis indicated that 61% of accounts relied solely on single sign-on, 29% were exclusively password-based, and only 10% had the option of both single sign-on and password authentication. Nevertheless, 63% of accounts—regardless of the login method—incorporated some form of MFA. However, it was concerning to discover that the majority of these accounts relied on what Push Security categorized as “phishable MFA,” rendering them susceptible to bypass attacks like MFA fatigue and sophisticated phishing tactics. Moreover, a mere fraction (less than 1%) of accounts using single sign-on methods implemented “phishing-resistant MFA,” according to Push Security’s data.
Of particular concern were accounts that combined single sign-on and passwords, as this configuration paved the way for ghost logins and potential compromise if attackers were able to exploit the password through tactics like credential stuffing or brute-force attacks. Even in scenarios where single sign-on was utilized, the initial access to the identity provider often required a password login. Shockingly, 17% of these accounts did not have MFA enabled, leaving them vulnerable to exploitation if the password fell into the wrong hands.
Highlighting the critical nature of identity provider accounts, Push Security highlighted that 20% of these accounts lacked MFA protection, underscoring the urgent need for enhanced security measures in these areas. Equally concerning was the revelation that 9% of identities were found to have compromised, weak, or reused passwords without MFA enabled, rendering them highly susceptible to credential stuffing and phishing attacks.
In conclusion, the findings from Push Security’s analysis serve as a stark reminder of the vulnerabilities that pervade organizational identity management practices. As businesses continue to navigate the complexities of a digital landscape, fortified cybersecurity measures, particularly in the realm of identity protection, are paramount to safeguarding sensitive data and mitigating the risk of malicious cyber threats. An urgent call to action is sounded for organizations to reevaluate their current identity management strategies and fortify their security posture to withstand evolving cyber risks.