In a recent development, threat actors have been exploiting misconfigured JupyterLab and Jupyter Notebook servers to illegally stream sports events. Security firm Aqua conducted research and found that attackers were taking advantage of vulnerabilities in these popular data science tools to hijack environments, deploy live streaming capture tools, and replicate sports broadcasts on unauthorized platforms.
The misuse of JupyterLab and Jupyter Notebooks, which are widely used for data analysis and interactive data science tasks, highlights the importance of proper security configurations. Aqua Nautilus researchers detected these malicious activities by deploying honeypots that simulated real-world development environments.
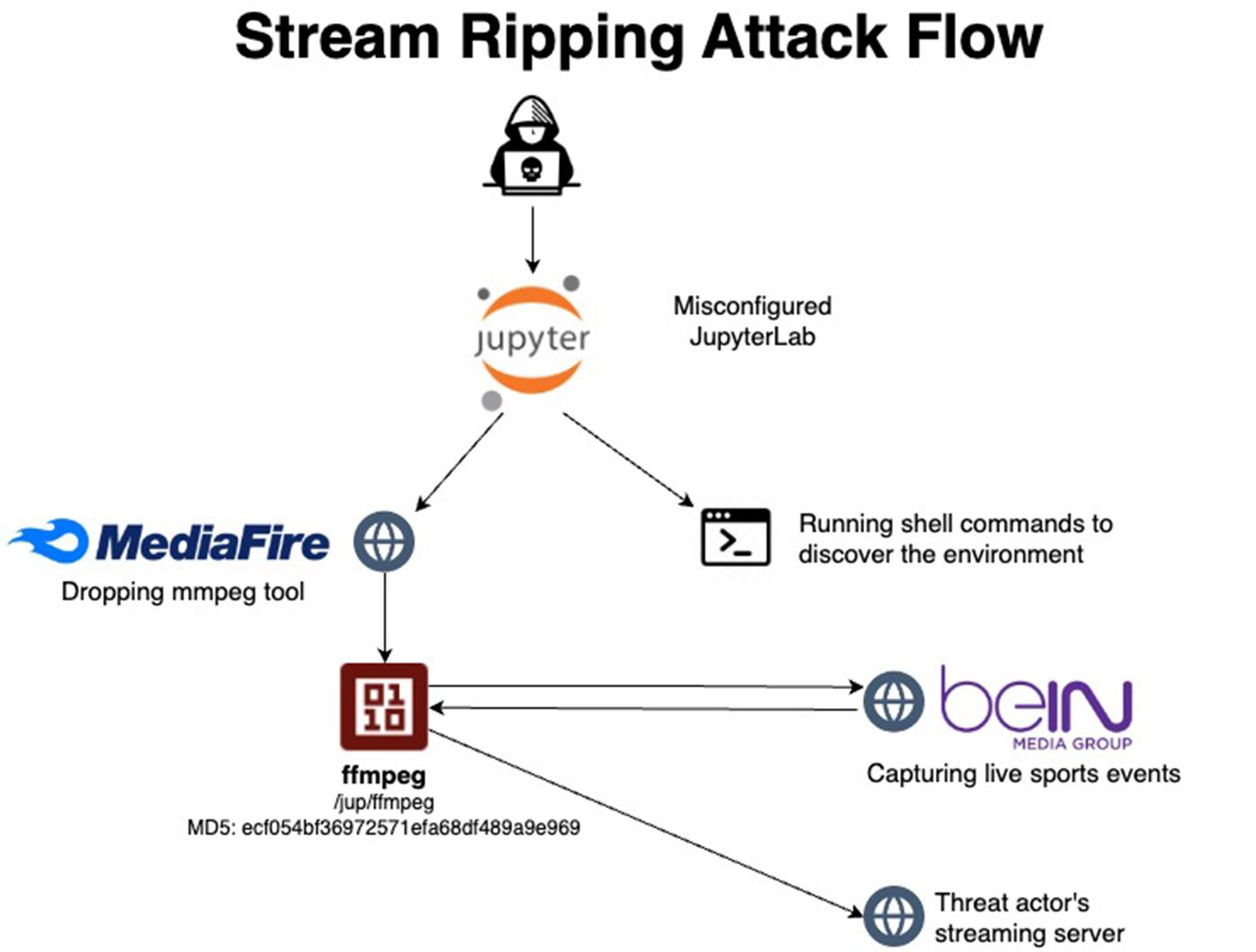
By analyzing outbound network traffic and running binaries in containerized environments, researchers were able to identify anomalies associated with illicit activities. One key finding was the use of ffmpeg, an open-source multimedia processing tool, which was being leveraged by threat actors to capture live streams of sports events and redistribute them on unauthorized servers.
The attackers gained initial access to the misconfigured servers by exploiting unauthenticated access and weak passwords on Jupyter Lab and Jupyter Notebook. The attack chain involved updating the server, downloading ffmpeg, capturing live sports feeds, and redirecting them to third-party streaming platforms.
While the impact on organizations may seem minimal at first glance, the repercussions of such unauthorized activities could be significant. The attackers could disrupt operations, manipulate data, steal sensitive information, compromise AI and ML processes, escalate their access to critical systems, and cause reputational damage to the targeted organizations.
In one specific incident analyzed by Aqua, threat actors downloaded ffmpeg from MediaFire and recorded live sports events from the Qatari beIN Sports network. The captured feeds were then redirected to a streaming platform called ustream.tv. The use of an IP address from an Algerian AS (41.200.191[.]23) hinted at a possible Arab origin of the threat actors involved in this illegal streaming operation.
Traditional security tools often struggle to detect such covert activities, especially in environments like JupyterLab and Jupyter Notebook where legitimate tools can be repurposed for malicious ends. By employing behavioral analysis to identify anomalies, Aqua’s research team was able to uncover these sophisticated sports piracy operations that circumvented standard security alerts.
It is crucial for organizations to prioritize secure deployment practices for data science tools and regularly audit their security configurations to prevent unauthorized access and misuse. By staying vigilant and adopting proactive security measures, businesses can safeguard their data, operations, and reputation from malicious actors who seek to exploit vulnerabilities for illegal purposes.