Phishing attacks are a prevalent cybersecurity threat that can be executed through various means, such as SMS, phone calls, and emails. However, the most common method involves sending victims emails containing malicious attachments. These attachments can come in different forms, such as executable files, office documents, archives, PDFs, or links.
Executable files are a simple yet obvious way for threat actors to conduct phishing attacks. By disguising malicious .exe files as legitimate documents or software updates, attackers can trick victims into opening them. These files are often delivered via emails that appear to be from reputable sources like banks or software vendors. Alternative executable types like .msi, .dll, and .scr files are also used to deceive victims with limited computer knowledge.
An example of a phishing executable in a sandbox environment reveals how AgentTesla malware is delivered through an .exe file disguised as a PDF. The fake name “BANK SWIFT.pdf____” is designed to confuse victims and persuade them to run the file.
Office documents are another common vehicle for phishing attacks, as they can contain embedded malicious macros, scripts, or exploits. By opening these documents, victims inadvertently execute malicious content that can lead to malware installation or data theft. An example of this is the exploitation of the CVE-2017-11882 vulnerability in Microsoft Equation Editor to infect systems with AgentTesla.
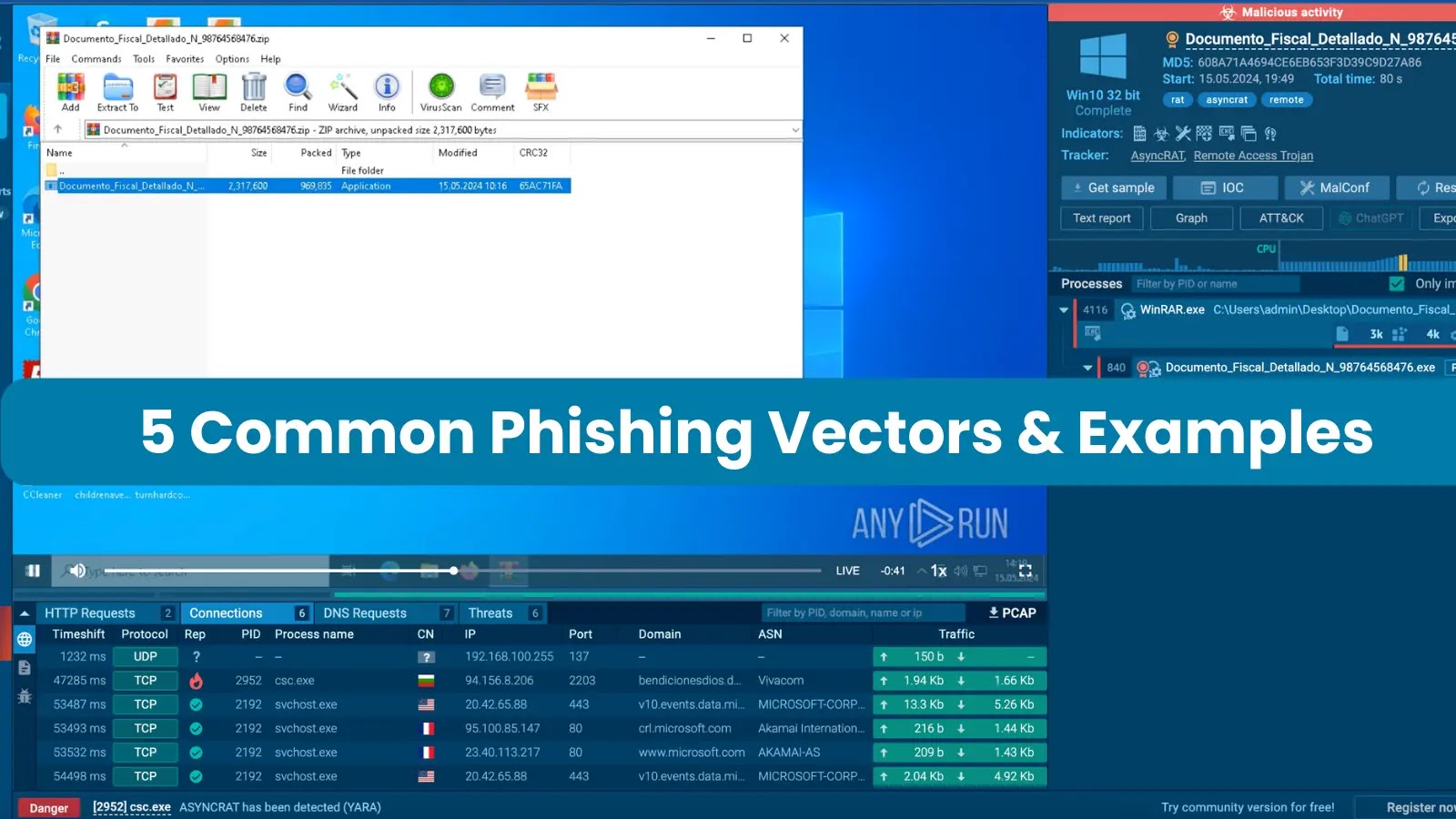
Archives are often used in phishing attacks to evade detection by security solutions. Threat actors may hide malware inside .ZIP or .RAR files to bypass scanning mechanisms. By using encryption, password protection, or various compression formats, attackers make it harder for security researchers to analyze the contents of the archive. An example of an archive-based phishing attack involving the deployment of AsyncRAT showcases how attackers use legitimate-sounding names to deceive victims.
PDFs are commonly used in phishing attacks by embedding them with malicious links that appear genuine. By clicking on these links, users can unknowingly download malware or have their personal information stolen. A sandbox analysis of a PDF file containing a phishing link illustrates how attackers use multiple stages to deploy malware payloads.
Malicious URLs sent via emails are a widespread phishing method, with cybercriminals often using tactics like URL shortening, typosquatting, and homograph attacks to create convincing links. By clicking on these links, victims may end up on fraudulent websites designed to steal their information or distribute malware. An example of a phishing attack involving a fake MS Outlook sign-in page demonstrates how attackers leverage legitimate services to make their pages appear trustworthy.
ANY.RUN’s cloud-based sandbox is an essential tool for analyzing phishing attacks, providing fully interactive Windows and Linux VM environments. By engaging with uploaded files and URLs, researchers can trace the attack, investigate network traffic, and gain insights into malicious activities. Additionally, users can access a special offer for six months of ANY.RUN Malware Sandbox Paid Plans for free until May 31st.
In conclusion, phishing attacks continue to pose significant risks to individuals and organizations, highlighting the importance of staying vigilant against malicious emails and attachments. By understanding the common methods used in phishing attacks and utilizing tools like ANY.RUN for analysis, users can better protect themselves from falling victim to these cyber threats.

