A highly sophisticated spyware campaign has been uncovered, targeting Apple iOS devices and leveraging never-before-seen exploits to bypass the company’s hardware-based security protections. The Russian cybersecurity firm Kaspersky, which discovered the campaign earlier in 2023 after becoming a target, described it as the “most sophisticated attack chain” it has ever observed.
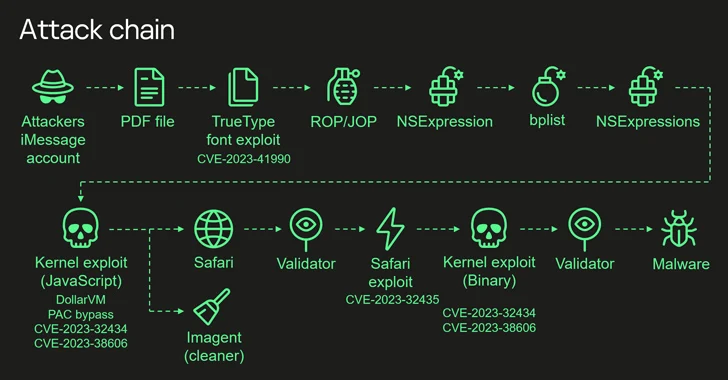
Dubbed Operation Triangulation, the spyware attack campaign has been active since 2019 and was named for the use of a fingerprinting technique called canvas fingerprinting to draw a yellow triangle on a pink background with Web Graphics Library (WebGL) in the device’s memory. The attackers leveraged four zero-day flaws fashioned into a chain to obtain an unprecedented level of access and backdoor target devices running iOS versions up to iOS 16.2 with the ultimate goal of gathering sensitive information.
The zero-click attack starts with an iMessage bearing a malicious attachment, which is automatically processed without any user interaction to ultimately obtain elevated permissions and deploy a spyware module. There are four specific vulnerabilities exploited in the attack – CVE-2023-41990, CVE-2023-32434, CVE-2023-32435, and CVE-2023-38606 – each allowing for various methods of arbitrary code execution and gaining unauthorized access to sensitive system components.
Apple has released patches for some of these vulnerabilities, but details about the exploitation were only made public by the company on September 8, 2023 – the same day it shipped an update to resolve two other actively exploited flaws. The company has emphasized the seriousness of the attack chain, stating that a total of 20 zero-day vulnerabilities have been actively exploited since the start of the year.
Of the four vulnerabilities, CVE-2023-38606 is particularly noteworthy as it allows a bypass of hardware-based security protection for sensitive regions of the kernel memory by leveraging memory-mapped I/O (MMIO) registers, a feature that was previously unknown. The exploit targets Apple A12-A16 Bionic SoCs and enables the threat actor to gain total control of the compromised system.
Security researchers have expressed surprise at the existence of this unknown hardware feature and its potentially unintended use. They believe that the feature may have been intended for debugging or testing purposes by Apple engineers or the factory, or it may have been included by mistake. The discovery emphasizes the flawed nature of “security through obscurity,” highlighting that all secrets are eventually revealed, and such systems can never truly be secure.
In a related development, it was reported that Apple’s warnings about state-sponsored spyware attacks targeting Indian journalists and opposition politicians prompted the government to question the veracity of the claims and describe them as a case of “algorithmic malfunction” within the tech giant’s systems. The Indian government reportedly demanded that Apple soften the political impact of the warnings and provide alternative explanations for their issuance.
So far, India has neither confirmed nor denied using spyware such as those by NSO Group’s Pegasus, despite Amnesty International finding evidence of Pegasus spyware activity on the iPhones of prominent journalists in the country. The revelations have brought attention to the lack of accountability over the use of spyware in India and raised concerns about human rights violations.
The article offers a glimpse into the ongoing challenges of hardware and software security, and the significant impact that state-sponsored spyware campaigns can have on individuals and organizations. The increasing sophistication of such attacks calls for greater vigilance and cooperation between technology companies and security experts to protect against future threats. Stay informed about developments in tech security by following us on Twitter and LinkedIn for more exclusive content we post.
In conclusion, the discovery of the Operation Triangulation spyware campaign targeting Apple iOS devices highlights the increasingly complex nature of cyber threats and the importance of implementing robust security measures to safeguard sensitive information. As cyber attackers continue to evolve their tactics, it is crucial for technology companies and security experts to work together to stay ahead of malicious activities and protect users from potential harm.

