A download manager site served Linux users malware that stealthily stole passwords and other sensitive information for more than three years as part of a supply chain attack.
The modus operandi entailed establishing a reverse shell to an actor-controlled server and installing a Bash stealer on the compromised system. The campaign, which took place between 2020 and 2022, is no longer active.
“This stealer collects data such as system information, browsing history, saved passwords, cryptocurrency wallet files, as well as credentials for cloud services (AWS, Google Cloud, Oracle Cloud Infrastructure, Azure),” Kaspersky researchers Georgy Kucherin and Leonid Bezvershenko said.
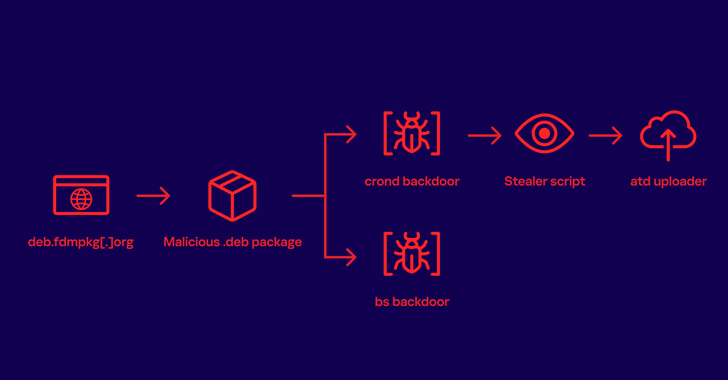
The website in question is freedownloadmanager[.]org, which, according to the Russian cybersecurity firm, offers a legitimate Linux software called “Free Download Manager,” but starting in January 2020, began redirecting some users who attempted to download it to another domain deb.fdmpkg[.]org that served a booby-trapped Debian package.
It’s suspected that the malware authors engineered the attack based on certain predefined filtering criteria (say, a digital fingerprint of the system) to selectively lead potential victims to the malicious version. The rogue redirects ended in 2022 for inexplicable reasons.
The Debian package contains a post-install script that’s executed upon its installation to drop two ELF files, /var/tmp/bs and a DNS-based backdoor (/var/tmp/crond) that launches a reverse shell to a command-and-control (C2) server, which is received in response to a DNS request to one of the four domains –
- 2c9bf1811ff428ef9ec999cc7544b43950947b0f.u.fdmpkg[.]org
- c6d76b1748b67fbc21ab493281dd1c7a558e3047.u.fdmpkg[.]org
- 0727bedf5c1f85f58337798a63812aa986448473.u.fdmpkg[.]org
- c3a05f0dac05669765800471abc1fdaba15e3360.u.fdmpkg[.]org
“The communication protocol is, depending on the connection type, either SSL or TCP,” the researchers said. “In the case of SSL, the crond backdoor launches the /var/tmp/bs executable and delegates all further communications to it. Otherwise, the reverse shell is created by the crond backdoor itself.”
The ultimate goal of the attack is to deploy a stealer malware and harvest sensitive data from the system. The collection information is then uploaded to the attacker’s server using an uploader binary downloaded from the C2 server.
crond, Kaspersky said, is a variant of a backdoor known as Bew that has been in circulation since 2013, while an early version of the Bash stealer malware was previously documented by Yoroi in June 2019.
It’s not immediately clear how the compromise actually took place and what the end goals of the campaign were. What’s evident is that not everyone who downloaded the software received the rogue package, enabling it to evade detection for years.
“While the campaign is currently inactive, this case of Free Download Manager demonstrates that it can be quite difficult to detect ongoing cyberattacks on Linux machines with the naked eye,” the researchers said.
“Thus, it is essential that Linux machines, both desktop and server, are equipped with reliable and efficient security solutions.”
-REFERENCE: https://thehackernews.com/2023/09/free-download-manager-site-compromised.html
-K.Z


